A new virus has been detected by our Security Malware Scanner on one of our client’s websites. So, using this file we created a malicious code signature and added it to the Security Malware Scanner.
<?php
/**
* Front to the WordPress application. This file doesn't do anything, but loads
* wp-blog-header.php which does and tells WordPress to load the theme.
*
* @package WordPress
*/
/**
* Tells WordPress to load the WordPress theme and output it.
*
* @var bool
*/
define( 'WP_USE_THEMES', true );
/** Loads the WordPress Environment and Template */
require __DIR__ . '/wp-blog-header.php';
eval('$some=1;');Here it is in the last line.
So, from this moment this virus will be recognized and auto-cured on all the websites, protected by our Website Security plugin.
What is a signature
A Signature is a specific pattern that allows cybersecurity technologies to recognize malicious threats such as SQL injections, malware etc.
There are different types of signatures in our Security plugin, including parts of malicious php/js/html code, entire files, and WAF (Web Application Firewall) rules.
How it works
In other words, the Signature is a kind of mold of the file, the scanner will create a mold of each file from your website (we work only with MD5 cache of files) and compare it with the signature mold (MD5 cache as well). And if it finds a match – the file will be marked as Critical. If the Cure malware option is enabled then automatic treatment is performed.
In order to enable the Cure malware option you should go to your WordPress Dashboard → Plugins → Security by CleanTalk → General Settings. You will find the option in the Malware Scanner part.
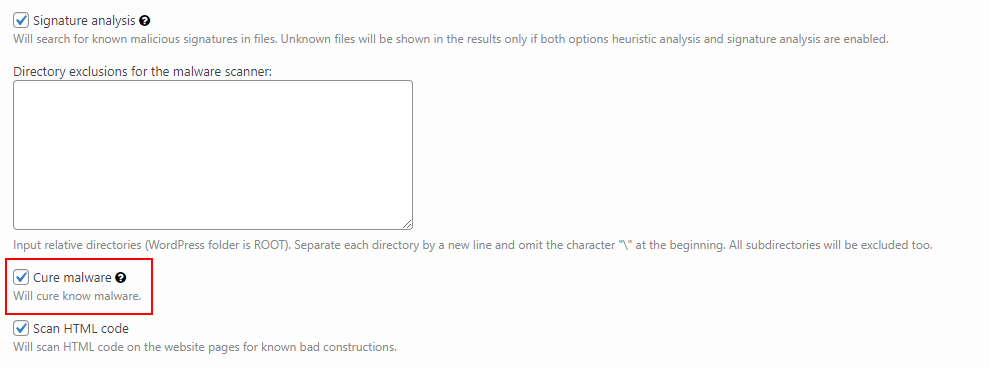
If you have any questions, add a comment and we will be happy to help you.



