This year the conference WordCamp Europe 2016 took place in Vienna and attracted more than 2300 guests. The capital of Austria is an excellent choice for such events, there are all conditions: convenient location, large meeting halls, and an active WordPress community. And there is something to see after the conference. Several of our developers have been on WordCamp Europe 2016. Under the cut – their story about the most interesting presentations and events.
The format of the conference
The conference lasted three days: the first two days we listened to the speeches, and the last day was given to the contributors. The reports were in different categories: Development, Design, Business, Content, Community, and took place in three streams, so everyone can find something interesting for yourself. Much attention speakers paid to high load questions, Continuous Integration, REST APIs, and the project Calypso.
On the day of contributors signed up about 600 volunteers. On this day it was possible to take a direct part in the development of WordPress, to learn how to work the kernel developers, translators, as well as the team checking the plugins and themes to the official catalog. You can even get advice on the organization of WordPress community in your city.
A nice bonus was the performance of Matt Mullenweg, the developer and the founder of WordPress, the founder of Automattic, WordPress.com, Akismet. But more on that below.
The most interesting report
PHP7 and WordPress
The release of PHP7 could not remain unnoticed at WordCamp Europe: how to provide the work of WordPress on PHP7, said Dan Blows in his report What’s New in PHP7 and what to expect in PHP7.1.
The core of WordPress and many plugins already support PHP7. Quoting the author, we can say: “Upgrade to PHP 7 easily, and probably everything will work immediately”. But he raised the points that should pay attention if you decided to migrate your website to PHP7.
The speaker told about innovations in PHP and the benefits that you can get when going to the seventh version. Dan showed impressive statistics of speed up of work WordPress on PHP7 compared to PHP 5.6.
A couple of reports about WordPress REST API
Especially important were the reports about REST API. This is one of the most important and actively developing directions. News from the developers WordPress rest API, about the difficulties and decisions is incredibly valuable information. Thanks Joe Hoyle and Adam White! Look at their performances The Ultimate REST API talk and Using the REST API and JavaScript to create better WordPress interfaces.
The reports disclosed the questions associated with use of the API and its development and expansion.
Now REST API is not yet part of the core, it exists in the form of a plugin. Adam in his report underlines the benefits that will get WordPress with integration of REST in its core. However, we now have the opportunity to build our apps using the new API.
The REST API gives unprecedented flexibility and expression “WordPress is limited only by your imagination” becomes a reality.
Dashboard Calypso
Due attention has been given to the relatively new development — Calypso. This is the administration panel of WordPress-sites, written in JS and running using WordPress REST API, which will definitely become popular.
Designer Calypso told about the project in general, and about what it cost for the team this his development and shared approaches in organization effective communication in the project. As Davide Casali said: “Communication is the oxygen”. It is impossible not to agree.
Experience of building a highly loaded WP-site
WordPress has long been used for the development of high-load news portals. Such giants as TED, TechCrunch, CNN, NBC built their sites on it. Yes, to build a high-load website is not easy, but speakers from NewsCorp Australia told how to do everything correctly.
Their experience – another precedent, proving the possibility of building on WP portals with millions of page views per day. Speakers gave valuable information about the development team and working process, talked about continuous integration, environment and visitor statistics. They also shared information that will help you to calculate the necessary costs for such a project.
Incredibly useful report, including from the point of view of communication with clients: How NewsCorp Australia scaled WordPress to host Australias largest ‘news’ websites on WordPress VIP.
About legacy-projects
Andrew Nacin — Lead-developer of WordPress core. With years of experience in the development of such a popular CMS system, the kernel developers have identified and summarized the key points of the philosophy of WordPress, which adheres and Andrew.
Get the big project “inherited” from people who have not really thought about the future is always difficult. And even painful. If you have such a project, the Andrew report will help to understand how to transform it in a stable and not require inappropriate investment product. Video of the report is available at the link.
Elasticsearch and ElasticPress
Full text search for MySQL databases by itself is not the best solution. But on high load sites and sites with large volumes of data — even more so. Elasticsearch is one of the solutions to implement an efficient search. How it works, how to configure Elasticsearch, how to protect data, and finally how to use it in your projects? These questions are answered by Taylor Lovett in the report Modernizing WordPress Search with Elasticsearch.
Taylor also tells about the plugin ElasticPress. The speaker is one of the developers of this plugin and knows what he’s talking about. In general, meetings with the developers of the components is always a unique opportunity to get information about the details of the use and future development plans.
The report about security
Of course, the most popular platform for developing websites in the world is one of the most attacked. So you need to constantly pay attention to the issue of information security.
Maurizio Pelizzone gave a presentation about securing WordPress websites: WordPress Hardening – Ten tips in ten minutes. The lecturer gave useful tips on how to reduce the risk to be hacked and sleep well.
Copywriting for professionals
At the end of the first day of the conference was the author of the best SEO-plugin for WordPress Joost de Valk and his wife Marieke van de Rakt. The report Beyond SEO – Copywriting for professionals, they told about the next stage in the evolution of search engines and the importance of high-quality texts.
Speakers against the “scorched earth tactics”. Joost and Marieke prefer sustainable and holistic approach to SEO, which involves focusing on all areas of optimization:
- The technical quality.
- Good UX & UI.
- Impeccable security.
- Great PR & Social
The basis of this approach is the high-quality content. And the principles of such content were presented in the report. In addition, the speakers spoke about a new functionality of their plugin, which allows you to make recommendations for improvement of the texts on your website.
Interview with Matt Mullenweg
Special attention deserves an interview with Matt Mullenweg: Interview and Q&A. the speech of Matt is a traditional part of WordCamp Europe. Right on the stage there is a sofa and provided almost homely atmosphere. In the second part of the perfomance, Matt talked to the audience.
They discussed potentially leading role REST API and interfaces on JS. Talked about the most successful and promising projects: Jetpack, WooCommerce and WordPress.com that do a lot for the success of WordPress in particular, and for an open Internet in general. Remembered about competitors, but Matt doesn’t consider them dangerous.
And much more
There were other interesting presentations, which we did not visit because we could not be simultaneously on all three streams. A complete list of video, as always, loaded on wordpress.tv.
Day contributors, how to develop core of WP
The conference was not limited by two days, full of interesting presentations and communication. For special interested was scheduled Contributor Day, which signed up about 600 people. It was held at the University of Vienna, Faculty of Informatics.
Each of the participants chose the direction in which he can get acquainted with the process of open-source development and to assist in the development of WordPress. Among the areas were: the development of the core, development of plugins and themes, internationalization, design, marketing, and support. Each group was coordinated by an experienced supervisor. The motto for the day was “Thank WordPress”. You could join the community, gain new experience, improve your professional level and make WordPress better.
The future of WordPress
WordPress is actively developed. The most interesting and promising areas — REST API and JavaScript interfaces. And the last were possible thanks to partly all the same REST API.
A lot of improvements in the core, for example, in recent releases significantly improved internationalization. Technology stack, development approaches, tools, and more — all have changed greatly since the advent of the first version of WordPress. There is movement forward, we are seeing regular releases that add something new.
Good news is that the core already supports PHP7. We already develop projects at NIX Solutions on a fresh PHP. But as for a full transition to the seventh version, here the prospect is not very encouraging. The fact that plugins and themes are supported by the community and by individual companies and not all of them in a hurry to implement support for PHP7.
What’s more surprising at the conference in Vienna is the maturity of the European community and a serious attitude to WP. We are sure that with such a large, active and talented community, WordPress has a great future.
Next WCEU 2017 in Paris
At the end of the conference, according to tradition, was announced the next city for WordCamp Europe, it became the capital of France. See you in Paris!
This text is a translation of the article “WordCamp Europe в Вене и вектор развития WordPress” published by @NIX_Solutions on habrahabr.ru.
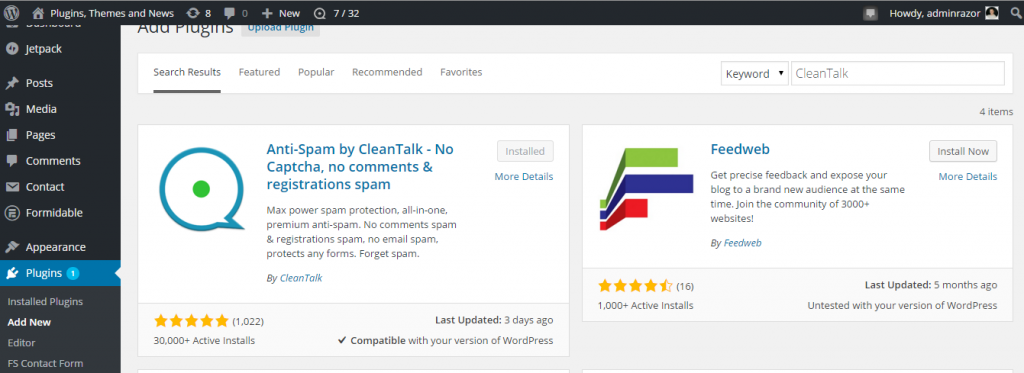
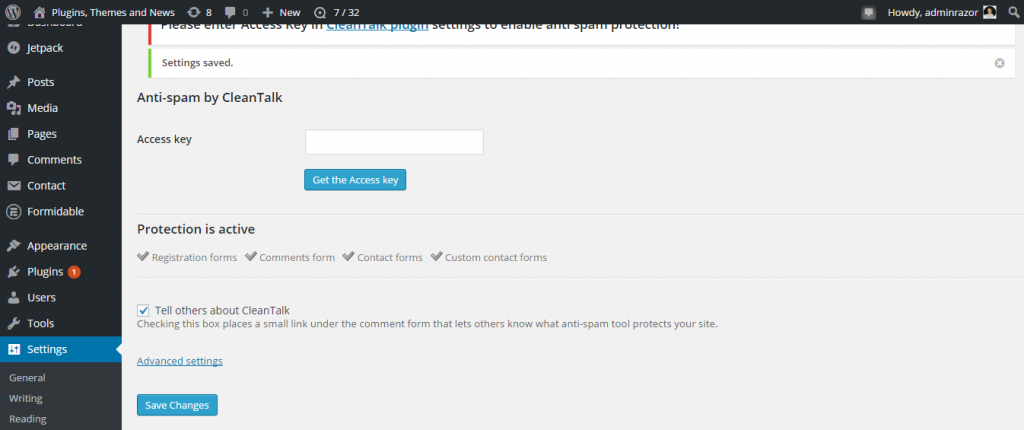
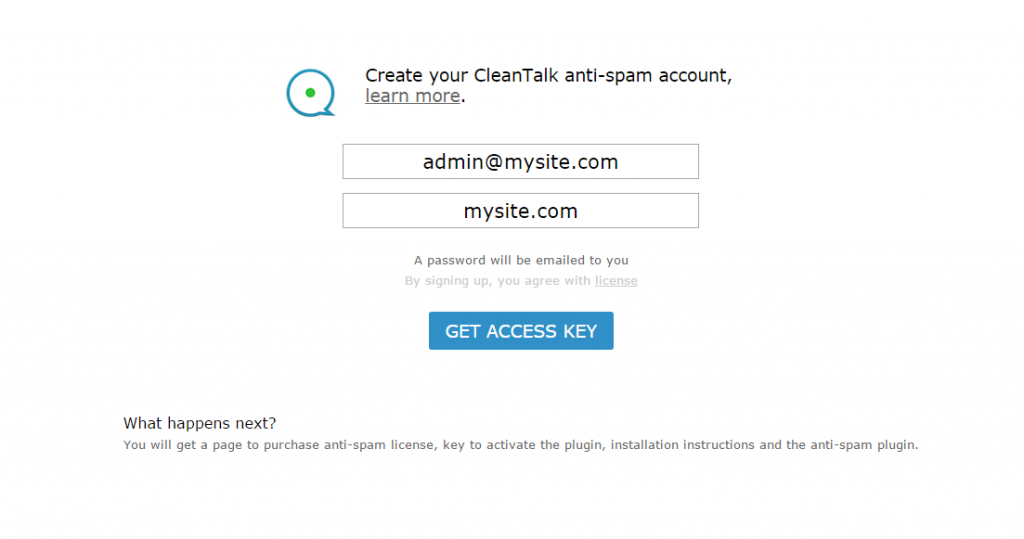
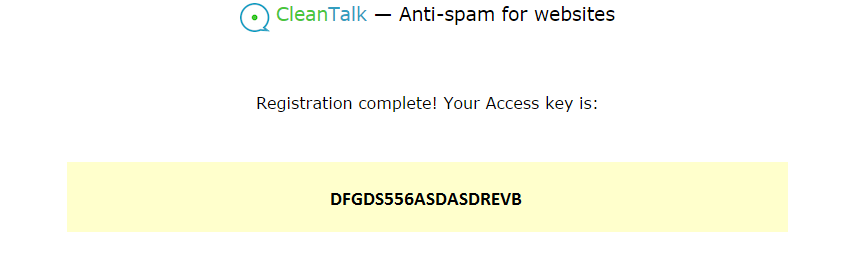
About the CleanTalk service
CleanTalk is a cloud service to protect websites from spam bots. CleanTalk uses protection methods that are invisible to the visitors of the website. This allows you to abandon the methods of protection that require the user to prove that he is a human (captcha, question-answer etc.).