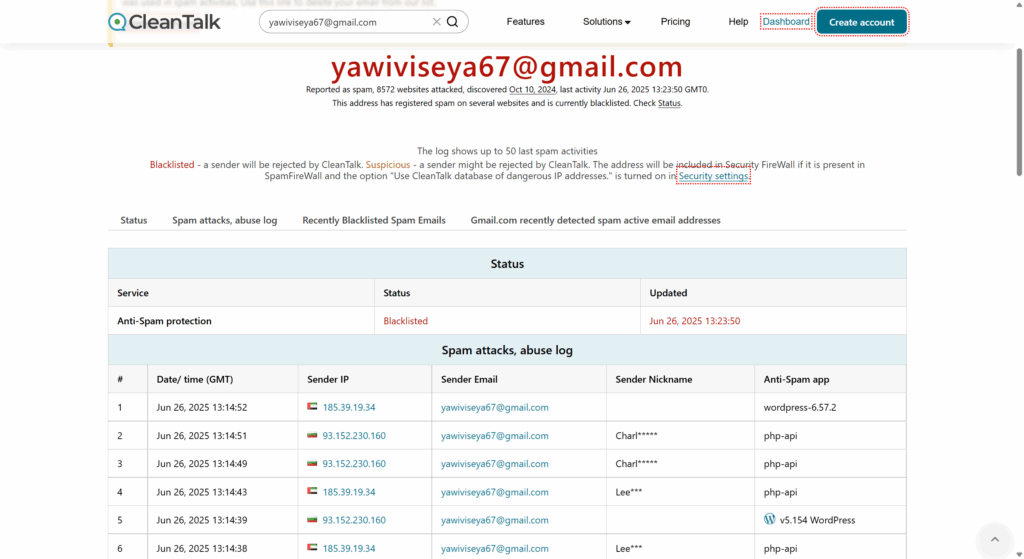
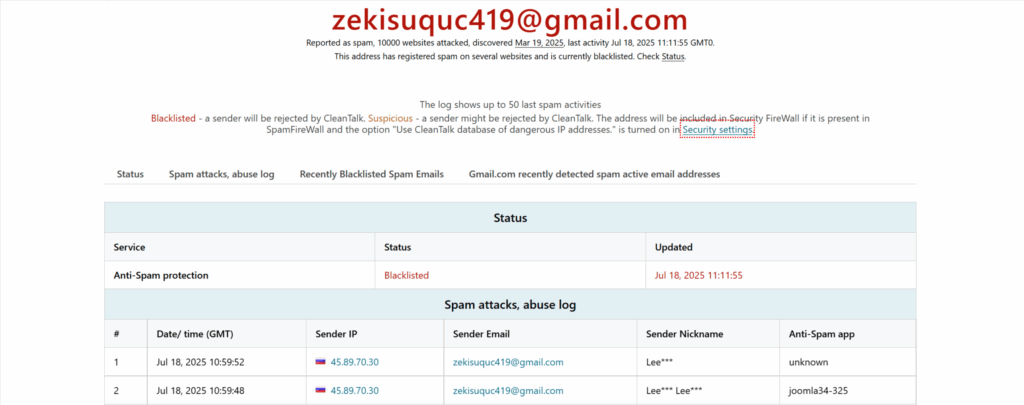
The email address zekisuquc419@gmail.com has been reported for sending spam and launching automated malicious requests on thousands of websites.
- According to CleanTalk BlackLists, this address has:
- Attacked over 10,000 websites
- Generated approximately 2,160 spam requests in the last 24 hours
- Used Russian IP addresses to send requests
- First detected on March 19, 2025
- Last activity recorded: July 18, 2025
Updated January 21, 2026
Attacked over 18,656 websites
Generated approximately 12,144 spam requests in the last 24 hours
What Does This Spam Bot Do?
This bot attempts to register accounts, submit forms, and post comments on websites using the email zekisuquc419@gmail.com. The activity is fully automated and intended to spread spam or malicious links. This can:
- Clutter your website with junk content
- Expose your visitors to phishing or malware
- Harm your SEO and domain reputation
This spam bot uses multiple languages to send what look like harmless price inquiries, helping it evade standard spam detection systems. At first sight, these messages seem genuine, which makes them especially dangerous for site administrators who could easily confuse them with real customer requests.
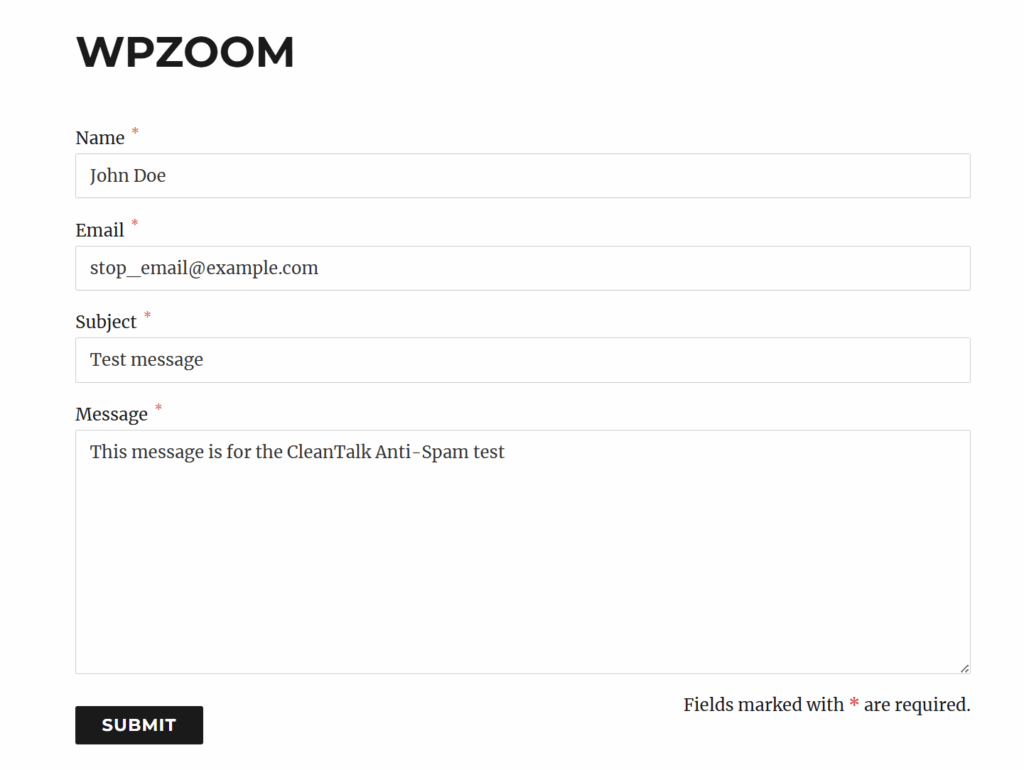
- Hi, I wanted to know your price.
- Прывітанне, я хацеў даведацца Ваш прайс.
- Salam, qiymətinizi bilmək istədim.
- Zdravo, htio sam znati vašu cijenu.
- Xin chào, tôi muốn biết giá của bạn.
- Aloha, makemake wau eʻike i kāu kumukūʻai.
- Ողջույն, ես ուզում էի իմանալ ձեր գինը.
- Kaixo, zure prezioa jakin nahi nuen.
- Hola, volia saber el seu preu.
This bot uses this template to submit contact forms.
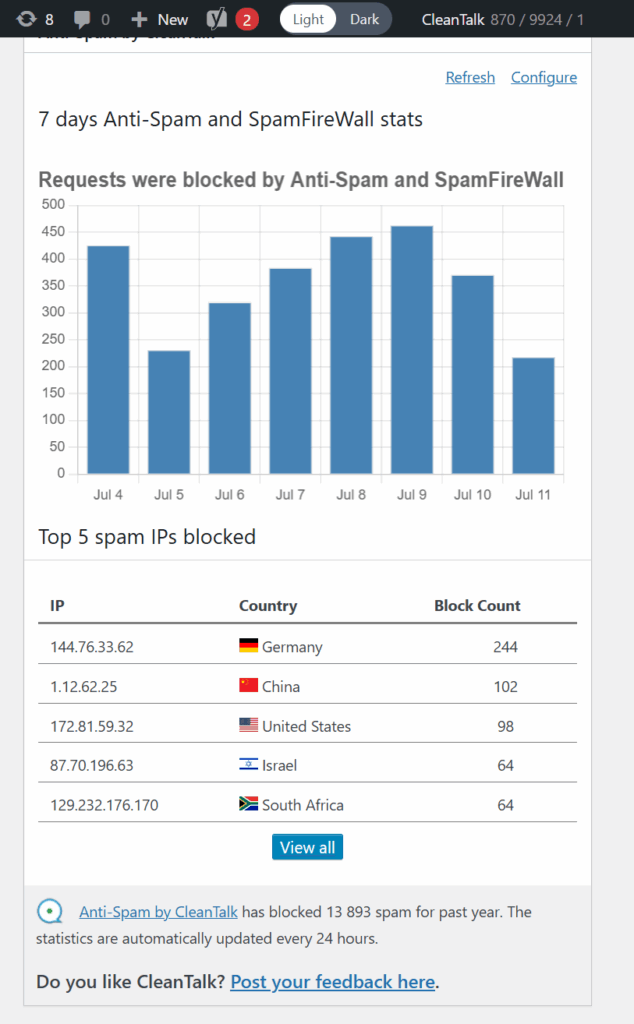
Here is a snapshot from CleanTalk’s logs:
“2160 requests in 24 hours detected from multiple Russian IP addresses. All actions associated with spam form submissions and bot-like behavior.”
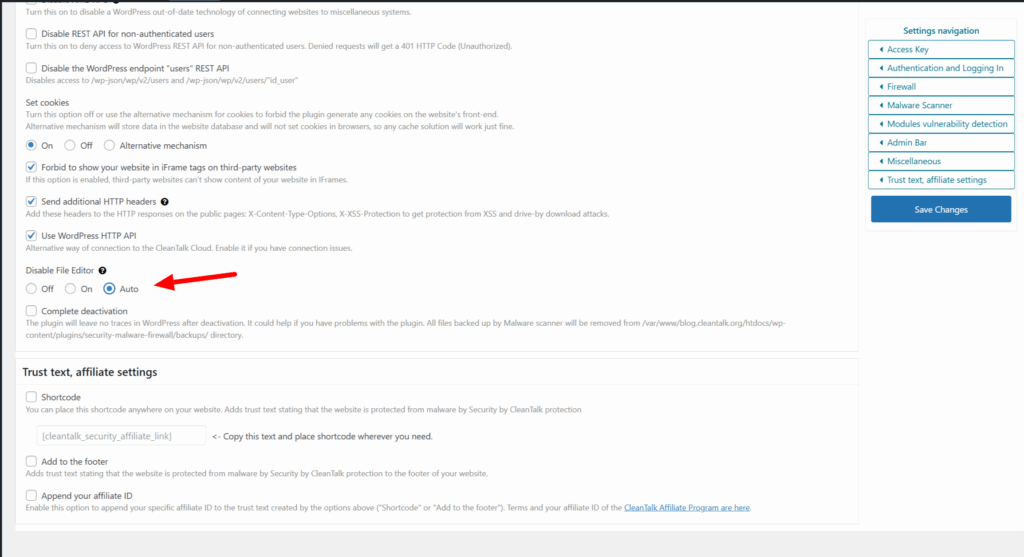
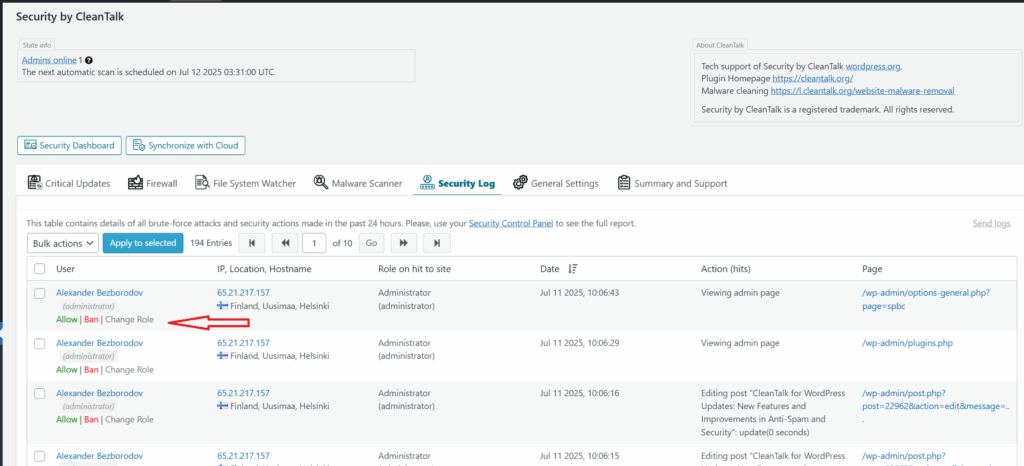
How to Block Spam from zekisuquc419@gmail.com
If you’re seeing traffic or spam submissions from this email, here’s how to stop it:
1. Use CleanTalk Anti-Spam Plugin
Install the CleanTalk Anti-Spam plugin for your CMS (WordPress, Joomla, Drupal, etc.). It automatically filters requests by checking emails, IPs, and behavior against the global CleanTalk Spam Database.
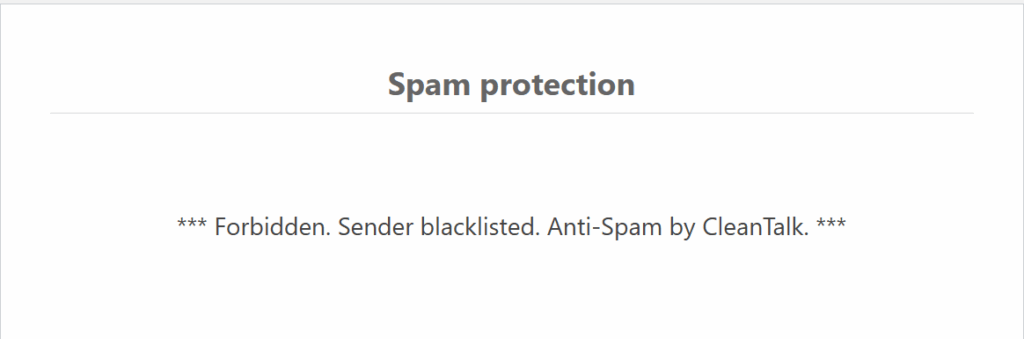
This email is already blacklisted and will be blocked automatically by the plugin.
2. Manually Block the Email (if needed)
If you want to block it manually in addition to using CleanTalk:
Add zekisuquc419@gmail.com to your site’s block list.
Block common IPs that were used in attacks (CleanTalk logs show many from Russian ranges).
Monitor your server logs for repetitive POST requests.
zekisuquc419@gmail.com is a known spammer attacking thousands of sites daily. By installing proper anti-spam protection like CleanTalk and staying vigilant, you can block these threats before they reach your visitors.
If you’re already using CleanTalk, rest assured — this spammer is on the blacklist and will be filtered automatically.
You can check any email or IP for spam activity on our BlackLists page.
🧩 Want full protection?
✅ Blocks fake registrations and spam submissions
✅ Filters bots and fake emails in real time
✅ No CAPTCHAs or puzzles – clean and fast
Stay ahead of spam – let CleanTalk handle the bots so you can focus on your content. Protect your site in under 5 minutes.
👉 Start now
Have you come across this kind of spam? Share your experience in the comments.