CleanTalk is a SaaS spam protection service for Web-sites. CleanTalk uses protection methods which are invisible for site visitors. Connecting to the service eliminates needs for CAPTCHA, questions and answers and other methods of protection, complicating the exchange of information on the site.
If you often read IT-news, you probably already tired of the horror stories about another vulnerability that was found in the popular OS / database / CMS / coffee maker. Therefore, this post is not about the vulnerability and about monitoring how people react to it.
But first – a few words about “the villain of the peace”. Critical vulnerabilities in popular WordPress blogging engine was found in September by the Finnish specialists from companies with funny name Klikki Oy. Using this hole, the hacker can lead as a comment to the blog a special code that will be executed in the browser of the site administrator when reading comments. Attack allows you to secretly take over the site and do unpleasant things under the admin access.
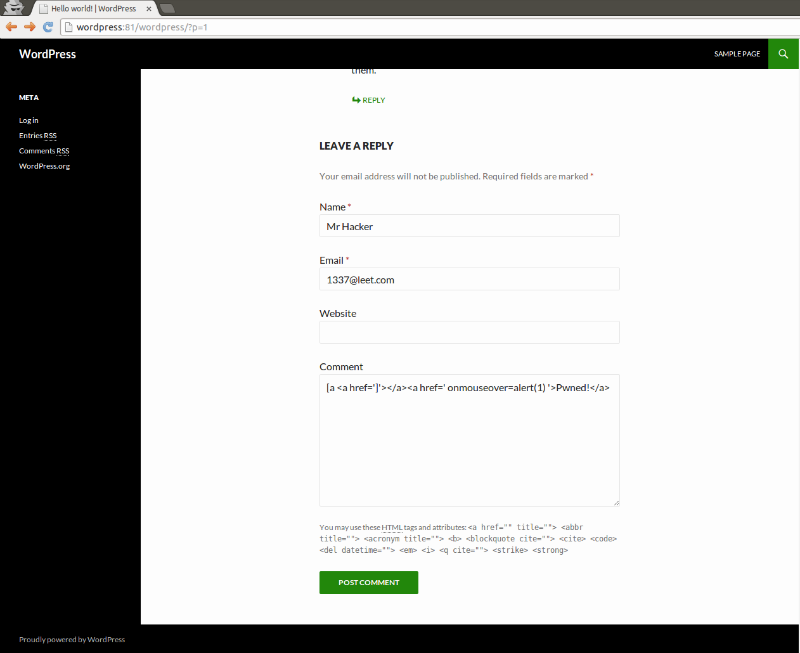
Here’s how easy it looks like in practice. Go to the blog by WordPress and enter a bad comment:
Next we see a specially crafted comment allows to bypass checks and conduct XSS-attack:
After capturing admin permissions an attacker can run their code on the server that is hosting the attacked blog, that is, can develop an attack on a broad front. Now is the time to remember that just recently 800,000 credit cards were stolen by a bank trojan which was distributed across WordPress sites.
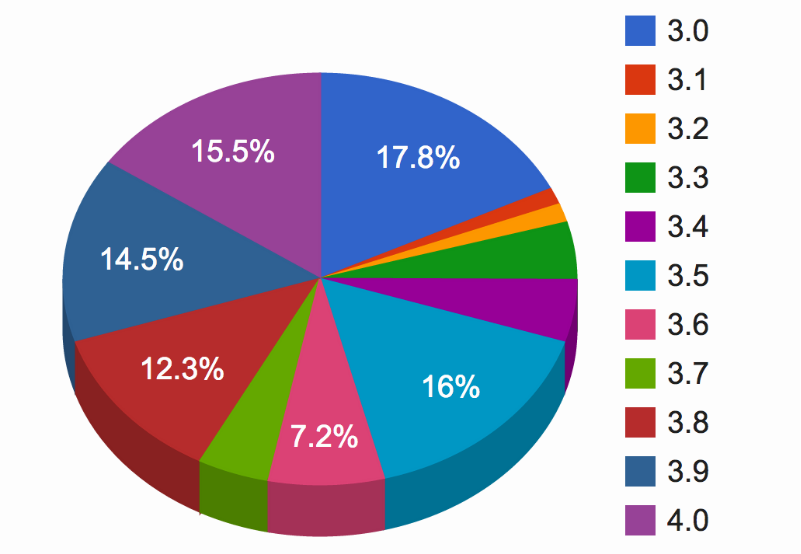
This vulnerability applies to all versions of WordPress 3.0 and higher. Problem can be solved upgrade engine to version 4, where no such problem.
And now about the actual reaction. Finnish security experts discovered a vulnerability reported it to the vendor on September 26. At the time of this writing, that is, two months later after finding renewed no more than 16% of users of WordPress (see diagram on the title picture post). What Finnish experts concluded that all the other 84%, that is tens of millions of users of this engine in the world, stay potential victims.
In fact, the victims will certainly be less because there is a small additional condition for the operation – need the opportunity to comment on posts or pages (default is available without authorization). However, we are interested in here is the lifetime of vulnerability, and in this case it is possible to observe in real time – to monitor the statistics update WordPress here. Although you probably already understand the meaning of these figures: don’t lock the barn door after the horse is stolen.
We also follow the intruders attempt to exploit this vulnerability “in the wild”. To do this, use a network attack detection based applications PT Application Firewall. The mechanism of intrusion detection based on the analysis of anomalies in this case worked well, and we did not have to add the signature. In other words, PT AF elicited this “0 day” from the very beginning:
At the moment, the vulnerability exploitation attempts is already found. They can not be called mass – but if you have an older WordPress, should still be updated.
This text is a translation of article “84% сайтов на WordPress могут быть взломаны: что дальше?” by ptsecurity published on habrahabr.ru.
Forums and blogs without spam
CleanTalk is a SaaS spam protection service for Web-sites. CleanTalk uses protection methods which are invisible for site visitors. Connecting to the service eliminates needs for CAPTCHA, questions and answers and other methods of protection, complicating the exchange of information on the site.


Leave a Reply