“… you come to me, and you ask something, but you don’t ask with respect …”
Vito Corleone
Phishing is still the most popular and most successful type of hacker attacks. It’s simple, attacked is not the software, not servers, not networks, and the most vulnerable components of information systems – users. I often meet with phishing, as a single, to personal addresses, and mass attacks. In most cases, it is awkwardly composed letters and clumsily made phishing pages. Until recently most of these attacks frustrated at the user level: letters or just ignored (as the signs of phishing was very obvious) or in the worst case, the letters are forwarded to customer support with the question “is it safe to enter your password on this page?”. Of course, some part of users still underway, but in percentage terms, it was really low. But just last week I was faced with a phishing attack, which surprised me. I did some analysis and found out how it was organized and what tools were used.
I hope it doesn’t look like the instructions for the preparation of phishing attacks; in fact, the purpose of this article is to tell you about a specific case from practice. I will also share the results of a small analysis of the actions of criminals.
Phishing page
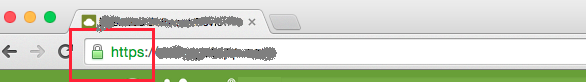
I’m not going to follow the sequence (as already mentioned, this is not a guide to action), and begin with the fact that surprised me the most, namely a fake page, which directed victims of the attack. The page was an exact copy of the ADFS page of the victim. In addition to visual similarity, the page was at the same level domain and URL, differ only by one letter: the real address of the ADFS portal was
, the address of the phishing page –
(hereinafter — the company name is replaced with contoso). And yes, the protocol is the same, a phishing page used SSL with a full certificate from COMODO!.. Of course, without Extended Validation, but nevertheless, Chrome displays the address of the “green”.
“Investigation”
How so? Very stupid “hackers”! Second level domains and certificates COMODO not given to anybody, they will be easy to calculate! But it is at first glance…
Domain
Google suggested that .cf domains distributed absolutely free. In this case, it is important not the price, and the opportunity to purchase the domain without leaving traces in the form of a credit card (or other payment method). That is, the usual (left) e-mail address is more than enough. One of the registers, Freenom, in addition to cf, offers, and tk, ml, ga. The only inconvenience, at the registration fails to specify some of free email (mail.ru, yandex.ru, yahoo.com), but you can register a domain with most other addresses.
Which mail was used by our Fisher to register a domain we couldn’t know as whois server gave this message: “Due to restrictions in [] Privacy Statement personal information about the user of the domain name cannot be released”. However, we can assume, that protonmail as phishing messages are sent using this service. This is not surprising, as on protonmail you can register completely anonymously, and even if you involve the appropriate authorities for investigation, make protonmail to cooperate, as practice shows, is not so simple.
SSL certificate and hosting
Before this incident, we naively believed that to raise web server with valid ssl certificate from COMODO, not leaving any traces, it is impossible. As it turned out, it is not. In our case, the attackers have used Cloudflare. A small analysis of the proposed features of this free package from Cloudflare identified many opportunities for phishing.
- Fully anonymous registration. Email address (from the same protonmail) is more than enough. Theoretically, they can find out from which IP address was the registration/ent
ry, but I am more than sure that our attackers could easily hide the real address. - Free certificate from COMODO. It is not only free but is issued for a few minutes without any additional check.
- Hiding the real IP address of the web server. All traffic goes through Cloudflare (it’s first CDN service)
- SSL offloading. Real web server can run on non-secure http, using Cloudflare all traffic goes through SSL. This is important because free web hosting with HTTP is real to find, and for hosting with SSL support you have to pay (leaving traces).
And another fact: with rare exceptions, CA services to the domains of ga, cf, tk not signe certificates. In this case (even if you are not Fischer) Cloudflare solves the problem, through them the certificate is issued without any problems.
Unvalidated Redirects in the service of Phishing
Now the most interesting. In the phishing email, which in itself represented a masterpiece of social engineering, of course, was a link, but not on a phishing page. The link was to the company website, on the page with the vulnerability type Unvalidated Redirects. It may have been one of the reasons that the letter passed all anti-spam filters, in email to the address user@contoso.ch was the only link to
http://contoso.c
Is it possible to find them?
Without a doubt, we cannot find them. Could the “law enforcement” find them? You can try to request data from the Registrar or from Cloudflare and go to the same protonmail. If they cooperate, the maximum that you can get is an IP address. Is it possible to track down a criminal by the IP address? I doubt it.
Conclusion
We don’t know how many people are “buying” — they will not confess. In any case, we advise everyone to change their AD passwords. The company was highly recommended to enable two-factor authentication for ADFS with Custom Authentication.
P.S. And yet, I’m not sure that I would not have bought it – I was impressed by the level.
This text is a translation of the article “Фишинг на новом уровне: Cloudflare + Protonmail + Unvalidated Redirects – набор юного фишера” published by Emin Hüseynov on habrahabr.ru.
About the CleanTalk service
CleanTalk is a cloud service to protect websites from spam bots. CleanTalk uses protection methods that are invisible to the visitors of the website. This allows you to abandon the methods of protection that require the user to prove that he is a human (captcha, question-answer etc.).
Leave a Reply