MailChimp users often find that emails from their email newsletters end up in spam. The emails themselves, the headers and the text are fine, but still for some reason the emails end up in spam. Let’s try to figure out what the reason might be.
Why email from MailChimp going to spam
- Exclamation points or certain phrases in the subject line
E.g. “Make money”, “F r e e”, “Not spam” and many others. Try to avoid using triggering phrases like these ones. - The Unsubscribe Button is missed
Always remember, that in case the email is not relevant to the mailing recipient and there is no Unsubscribe button, then the only way for the recipient to stop getting the email is to mark it as spam. - Irrelevant offer
In case several people mark your email as spam, other emails can end up in the spam folder as well. - Blacklisted or unreal email in your email list
Having blacklisted and unreal emails in your email list can be recognized by spam filters and put your emails at risk of going into the spam folder. In the instructions below, we will tell you how to clean your mailing list of “bad” addresses.
How to keep MailChimp from going to spam
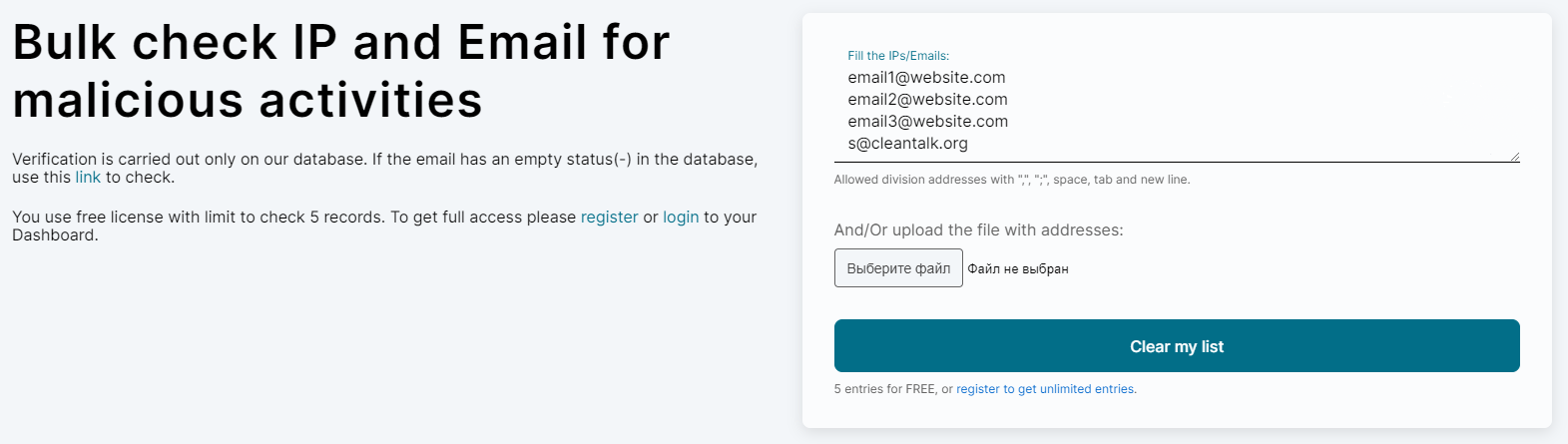
1. Go to SpamBots Check page, copy and paste the email list into the left field or you may upload the file using the Browse button on the right, and press the Submit button. You will need to register in order to check more than 5 emails, which takes about 30 seconds.
2. After that, you will see a list of checked emails with their results. Feel free to download CSV and JSON files or share a link to that check using the links on the upper right.
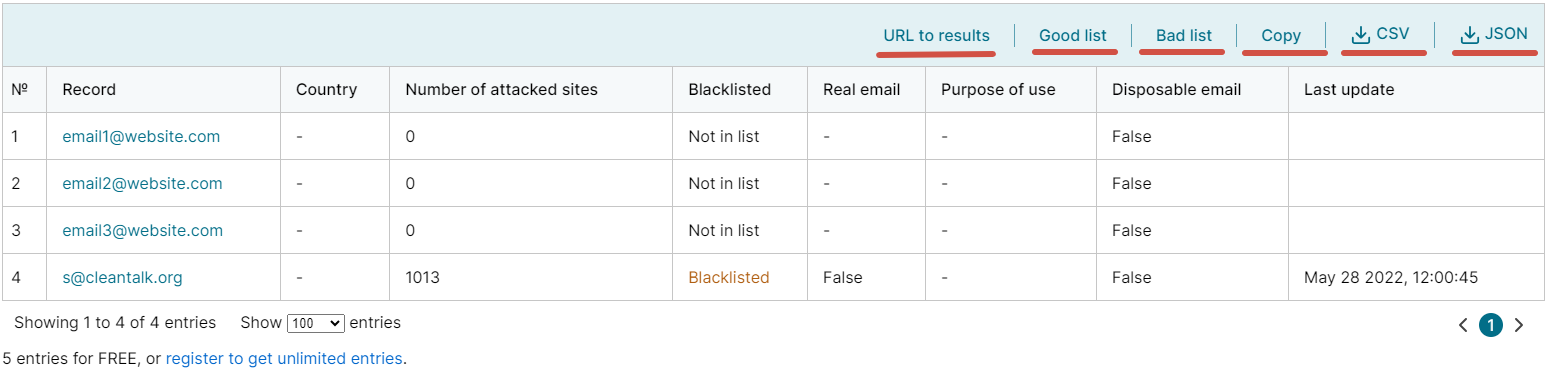
URL to results – share the check results or reset to full list, including both good and bad lists.
Good list – remove emails that are suspiciously active or invalid.
Bad list – leave only email that are suspiciously active or invalid.
Copy – copy the entire list of emails.
CSV – download results of the check in CSV-file.
JSON – download results of the check in JSON-file.
3. Go to CSV or JSON file and copy only emails, that are not blacklisted.
4, Go to your MailChimp newsletter, paste the list in there, and press the Continue to organize button.
5. After that, continue creating your MailChimp newsletter as usual.
Using only verified emails will help you avoid MailChimp going to spam and get more of your newsletter emails delivered and opened. And don’t forget to verify all your email lists to reduce the chances of your emails ending up in spam. Email verification not only allows assistance in cleaning email lists to increase email deliverability and engagement rates.