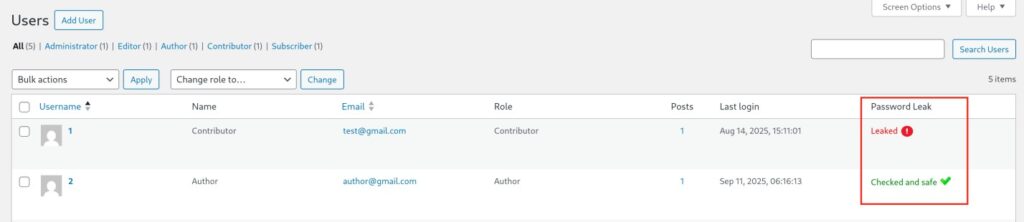
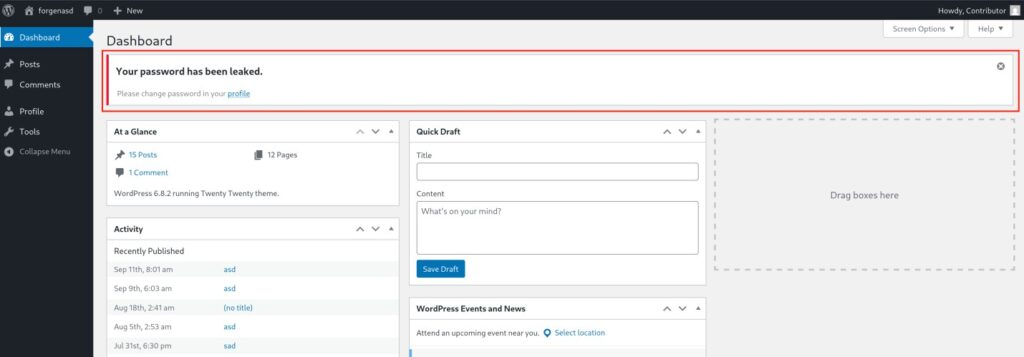
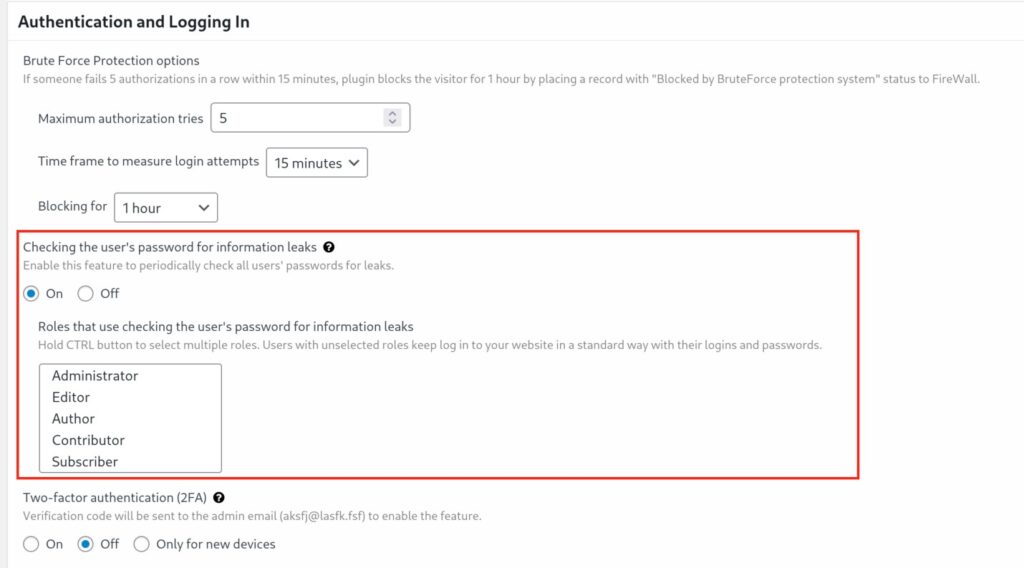
We’re reaching out to let you know about a security vulnerability that was recently disclosed in the CleanTalk Anti-Spam plugin for WordPress. We’ve already released a fix, and we want to make sure you’re protected.
What happened?
On February 14, 2026, a vulnerability (CVE-2026-1490) was publicly disclosed affecting CleanTalk Anti-Spam plugin versions 6.71 and earlier. The issue was found in the checkWithoutToken function, which relied on reverse DNS (PTR record) resolution to verify incoming requests. An attacker could spoof a PTR record to impersonate CleanTalk servers, potentially allowing them to install unauthorized plugins on a vulnerable site. In a worst-case scenario, this could lead to remote code execution through a chain of exploits.
Here’s the important part: this vulnerability only affects sites running with an invalid or expired or missing API key. If your CleanTalk subscription is active and your API key is valid, the exploitable code path is never triggered. That said, we strongly recommend updating regardless – it’s simply good practice.
What you need to do:
Update the plugin to version 6.72 or later – the fix is already available in the WordPress plugin repository
Verify your API key is active and valid in your CleanTalk dashboard at https://cleantalk.org/my or in your WP Dashboard->Settings->Anti-Spam by CleanTalk.
If you have auto-updates enabled, you may already be on the latest version — but please double-check
Keeping plugins up to date is the most effective way to maintain website security.
What we’ve done on our end:
We patched the checkWithoutToken function to no longer rely solely on PTR records for authorization. The updated verification process uses stronger validation methods that cannot be spoofed. The fix was released in version 6.72, which is available now.
References:
CVE record: https://www.cve.org/CVERecord?id=CVE-2026-1490
Wordfence advisory: https://www.wordfence.com/threat-intel/vulnerabilities/id/cb603be6-4a12-49e1-b8cc-b2062eb97f16
Plugin changelog: https://wordpress.org/plugins/cleantalk-spam-protect/#developers
A note from our team:
We take security seriously – both yours and our own. No software is immune to vulnerabilities, but what matters is how quickly they’re addressed and how transparently they’re communicated. We identified the issue, developed a fix, and released the update promptly.
We’re also conducting an internal review of similar patterns across our codebase to prevent this class of vulnerability from recurring.
If you have any questions or need assistance updating, our support team is here to help at support@cleantalk.org.
Best regards,
The CleanTalk Team