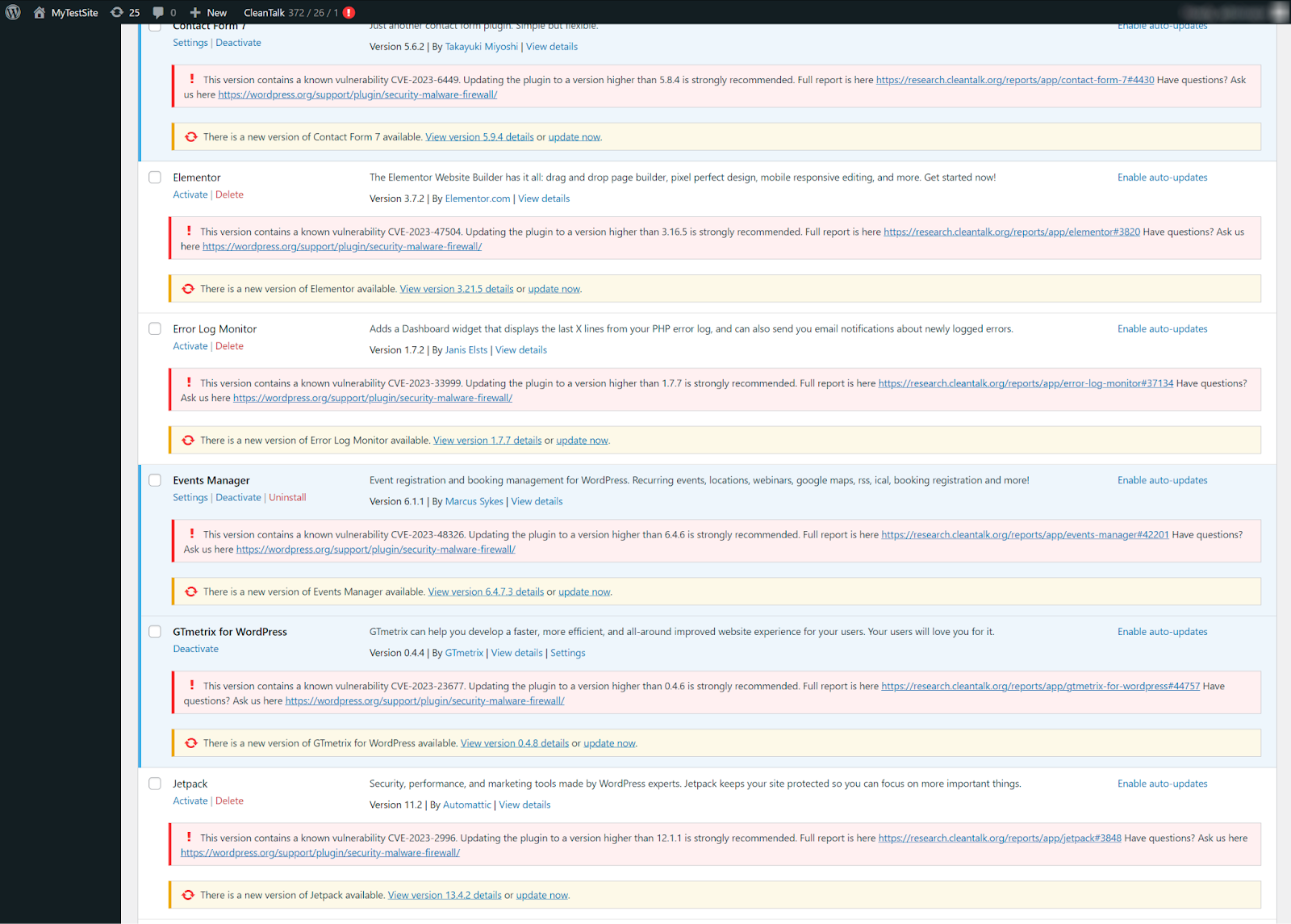
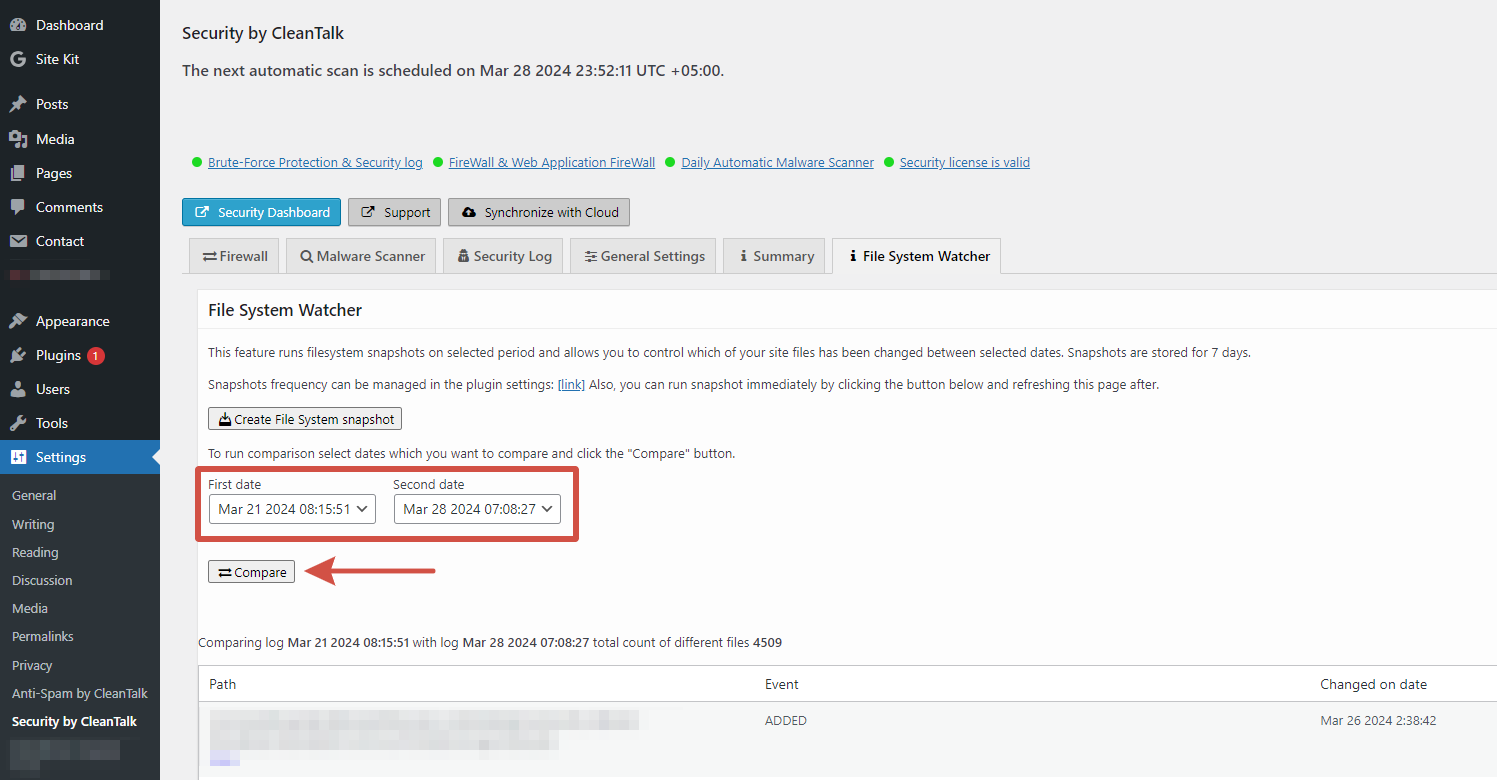
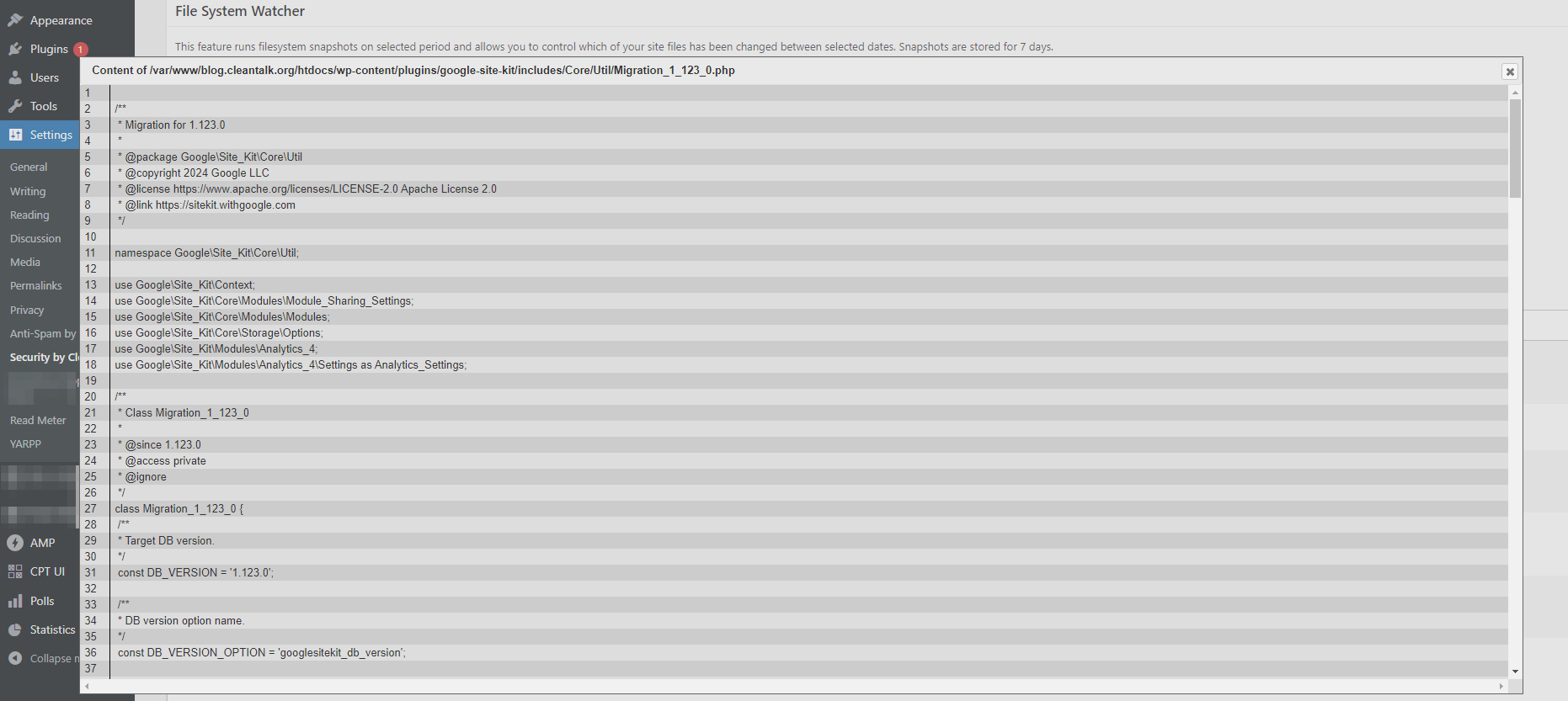
The CleanTalk Research Team identified a critical Stored XSS (Cross-Site Scripting) vulnerability in the WP SEOPress plugin, version 7.7.1. This flaw can be exploited by attackers with contributor privileges to create new admin accounts, potentially granting them full control of your WordPress website.
Understanding Stored XSS (CVE-2024-4899)
Stored XSS vulnerabilities allow attackers to inject malicious scripts directly into your website’s database. These scripts are then executed whenever someone views the compromised content. Unlike reflected XSS, user interaction isn’t required to trigger the attack, making it particularly dangerous.
How Attackers Can Exploit This Vulnerability
An attacker with contributor privileges can exploit this vulnerability by injecting malicious JavaScript code into the “SEO Title” field while creating a new post. This code can then be used to create a new admin account, granting them complete control over your website.
Potential Consequences of an Exploit
- Complete Site Takeover: Attackers could create new admin accounts and seize full control of your website.
- Data Theft: Sensitive information like user credentials, financial records, and even your website’s content could be stolen.
- Website Defacement: Attackers could alter the appearance of your site, inject further malicious code, or display unauthorized content.
- Persistent Backdoors: Malicious actors might install backdoors to ensure continued access even after the initial vulnerability is patched.
Taking Action to Secure Your Website
- Update Immediately: The most critical step is to update the WP SEOPress plugin to the latest version as soon as possible. This update addresses the vulnerability and safeguards your website.
- Review User Roles: Carefully review user roles and permissions. Contributors should have the minimum access necessary for their tasks.
Through continuous vulnerability discovery and disclosure, we empower website owners and developers to take preventative measures. We believe that by working together, we can create a robust and secure WordPress ecosystem for everyone.
Stay vigilant. Stay secure.