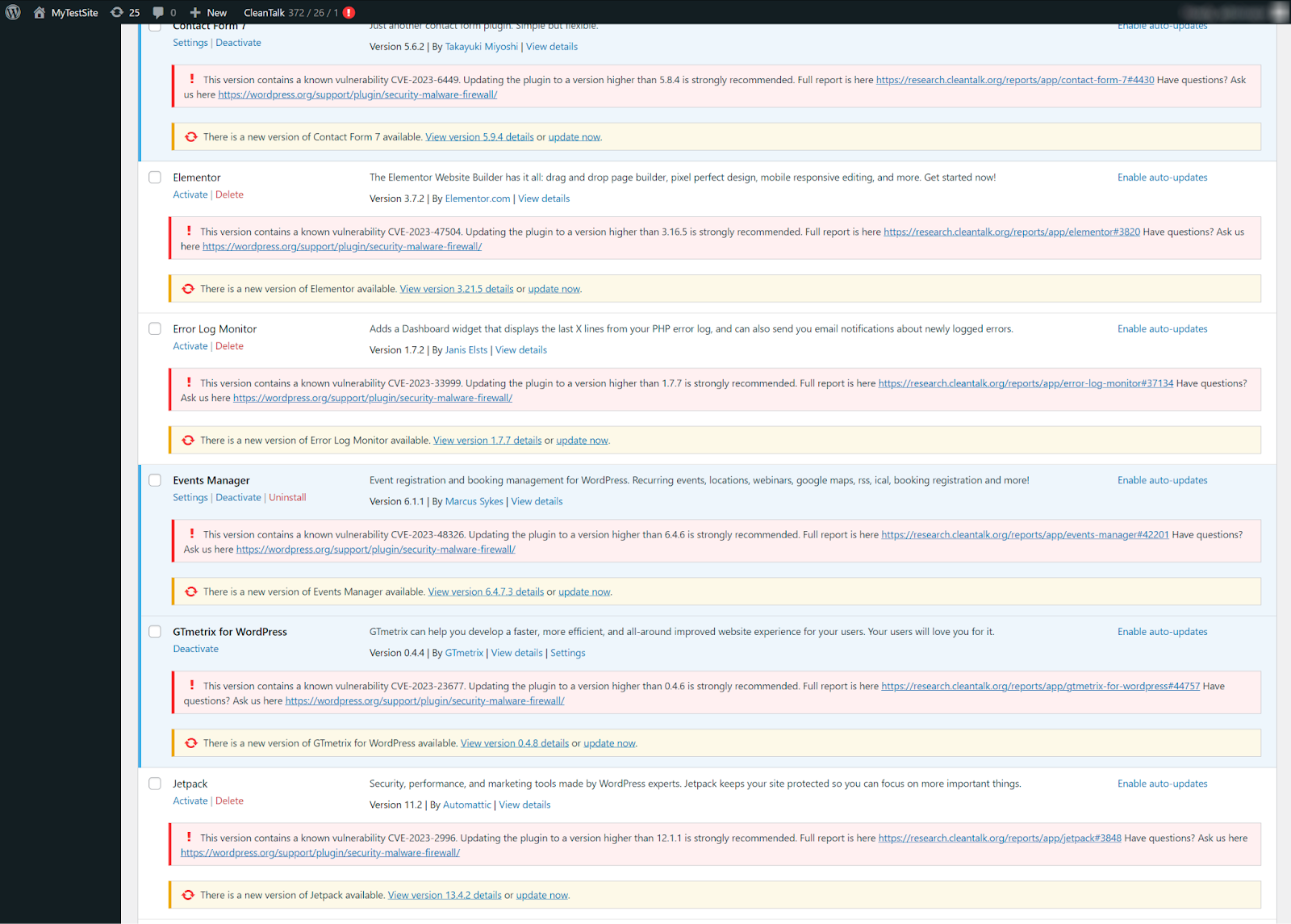
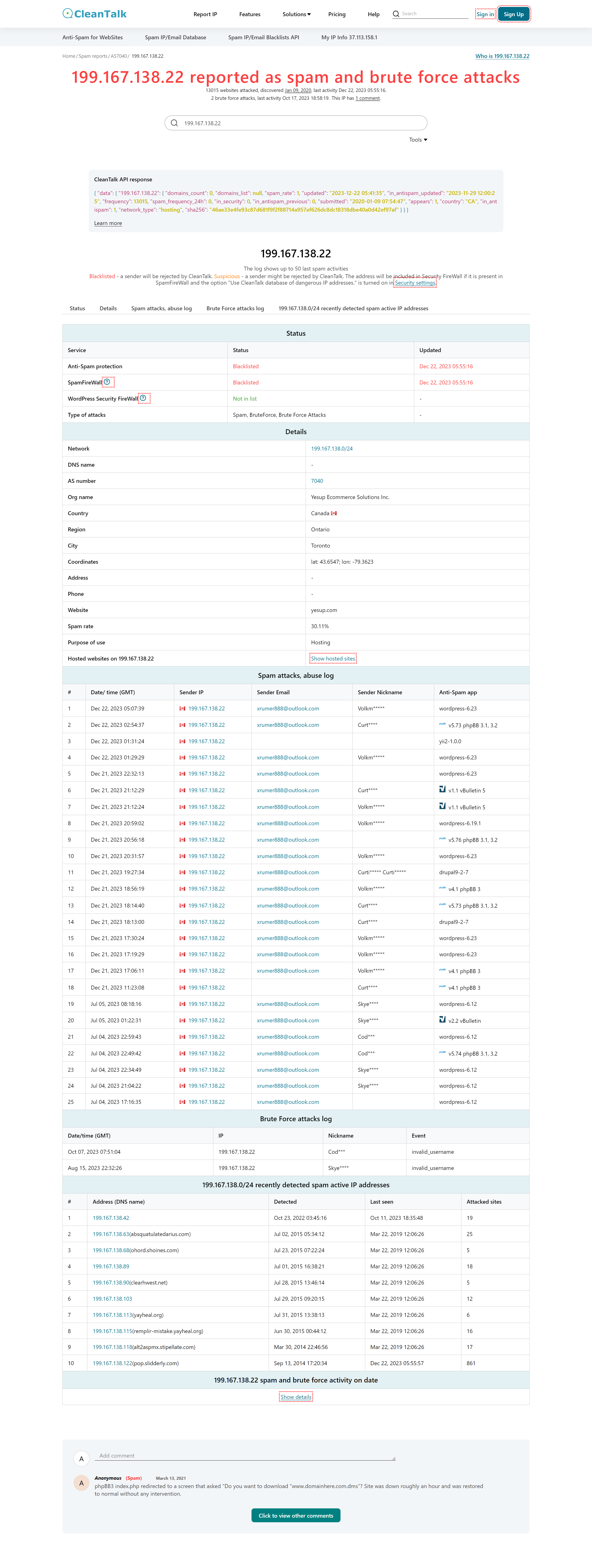
If your website was developed using one of the popular CMS like WordPress or others, there are various security plugins for them, which provide permanent protection from malware. But what to do if your site is unprotected and you suspect that it has been infected? Let’s find out together.
6 signs that your website may be infected

First of all, let’s break down when it’s really time for you to think about cleaning your site of malware.
- Unusual activity in Server logs
Server logs contain access logs that display the users who have recently accessed your website. - Your website is slow
Hackers deploy DoS attacks to overload your server resources, thus impacting your website speed and performance. - Emails ending in the Spam folder
This happens when your web server is infected with malware. As a result, email servers categorize your emails as “spam”. - Pop-up and Spam Ads
Usually happens when you have installed an insecure plugin or theme. Hackers earn money when visitor clicks on them. - Modified website files
To insert backdoors and other malicious code in your site, hackers often modify your website core files. - Website being redirected
Hackers often deploy cross-site scripting (or XSS) attacks to send your website traffic to unsolicited websites.
What is a manual malware removal
During a manual malware removal, a dedicated cybersecurity specialist is assigned to your site to work on your site from start to complete site cleanup.
Step 1: Clean up the bad stuff
Using SSH and admin access, the specialist reaches your website hosting and gets rid of all viruses, malware, malicious code, and bad links on your website.
Step 2: Restore the site from backup
In case you have a backup he restores the site from backup. Otherwise, he works with the site’s current version.
Step 3: Protect it from future infections
The specialist installs a permanent Security protection plugin to avoid infecting in the future.
Reasons to use manual malware removal instead of automatic

Sometimes automatic solutions can be enough to find the most known viruses and malware and often are low cost or free.
Automatic free malware removal tools can be effective at identifying and removing known malware from a website, but there are several reasons why they may not completely cure a website of all security threats.
- Over-insurance and possible data loss
The problem is that they often over-insure and accept your files as bad ones, causing large file and data losses during automatic site cures. A specialist can always distinguish your files from malicious ones even if it’s a custom code. - Evolving Malware
Malware is constantly evolving, with new variants and techniques being developed by cybercriminals. Automatic tools may not always be able to keep up with the latest malware threats. - Hidden Malware
Some malware is designed to be stealthy and can hide in obscure locations within a website’s code or files. Automatic tools may not always detect these hidden threats. - False Positives
Automatic tools may sometimes flag legitimate code or files as malware, leading to false positives. This can result in the removal of essential components of the website, causing functionality issues. - Complex Infections
In some cases, websites may be infected with complex malware that requires manual intervention to fully eradicate. Automatic tools may not have the capability to address these intricate infections effectively. - Vulnerability Patching
While malware removal tools can remove existing infections, they may not address the underlying vulnerabilities that allowed the malware to compromise the website in the first place. It’s essential to also address security vulnerabilities and implement robust security measures to prevent future infections. - Human Expertise
Manual inspection and intervention by cybersecurity experts are often necessary to thoroughly assess the extent of an infection, identify potential backdoors, and ensure that the website is fully secure.
In conclusion, while automatic malware removal tools are valuable for initial detection and removal of known threats, they may not be sufficient to completely cure a website of all security issues. Manual inspection, ongoing security measures, and expert intervention are often necessary to ensure comprehensive protection against malware and other security threats.
Why it is profitable for you to use CleanTalk malware removal
| 100% refund in case of unsuccessful We will manually clean your site from viruses and malware or refund your money. | 10+ years fighting malware of fighting malware and spam all over the Internet. We are aware of all the dangers that can threaten your website and how to deal with them. |
| 30-day support Free 30-day help with reinfection. As a guarantee of our work we continue to be with you and will get back to work if needed. | 50+ CVE reports published And we continue to share found vulnerabilities in our blog. |
| 10 000+ active users A lot of loyal users that trust our experience and use our Security protection. | 1 year of free Security Plugin Order your Malware Removal now and get 1 year of free Security plugin. |
Clean your site from malware today
And get CleanTalk Security Plugin for 1 year for FREE