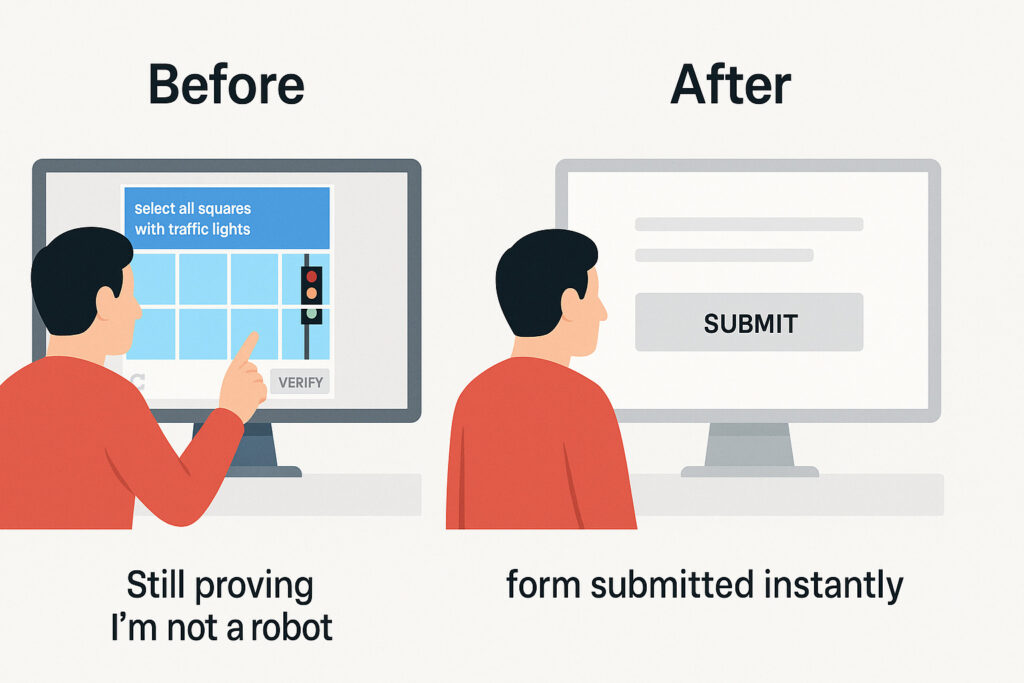
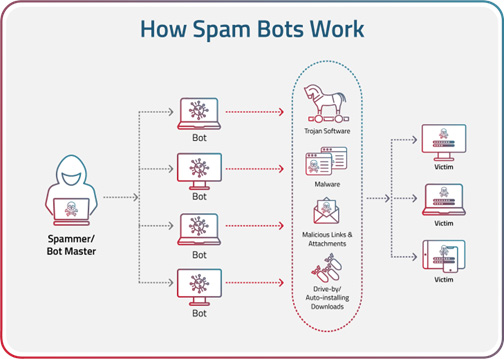
Leaked passwords are one of the fastest-growing threats to WordPress. WordPress password leak protection helps block attackers who reuse stolen credentials from massive breaches.Security by CleanTalk now gives you a way to stop them before they log in.
What’s New: WordPress Password Leak Protection
Password Leak Protection automatically checks user credentials against public breach databases. If a password is exposed, login is denied and the user is forced to reset it on the next attempt.
Update your plugin and turn it on in General Settings.
User experience
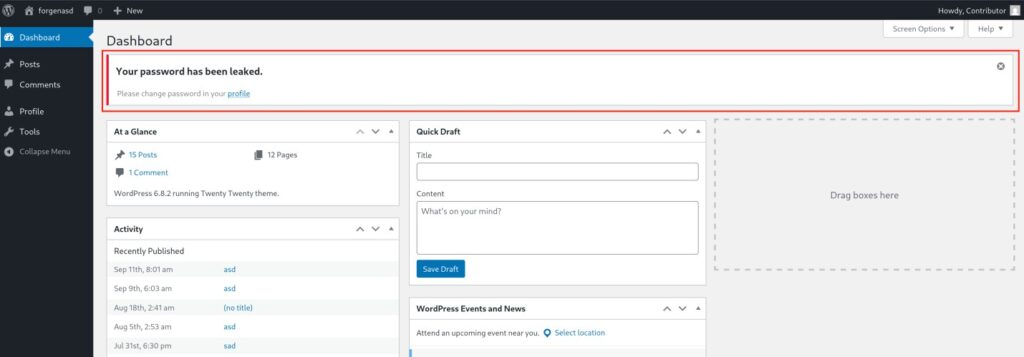
When a password is flagged as leaked, the next login takes the user to a compact reset form right on the login page. They enter the current password, choose a new one, confirm it, and can sign in again immediately. The leaked status is cleared after a successful change.
Administrator View: WordPress Password Leak Protection
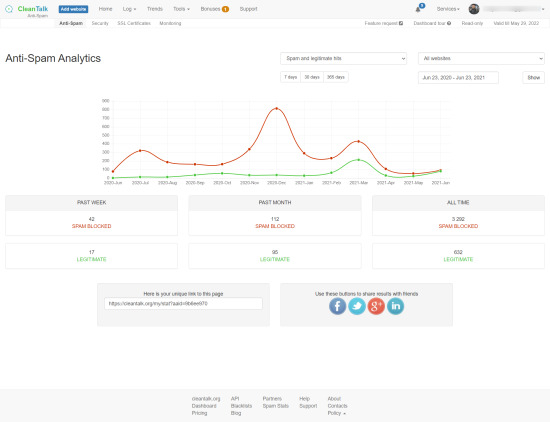
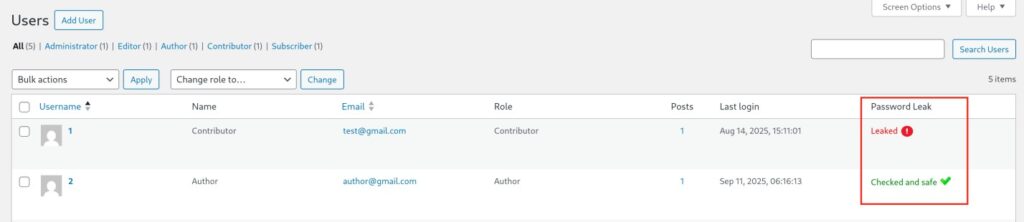
Administrators can monitor security directly inside WordPress, and WordPress password leak protection adds another layer of defense. The Users table now shows a Password Leak column with three possible statuses: Not verified, Safe, or Leaked. If the system finds compromised accounts, the dashboard shows a warning banner.. For additional control, administrators can run manual checks from the Users section, and results update instantly through AJAX. Background tasks run automatically in batches, ensuring that large sites are processed without extra load.
How to enable
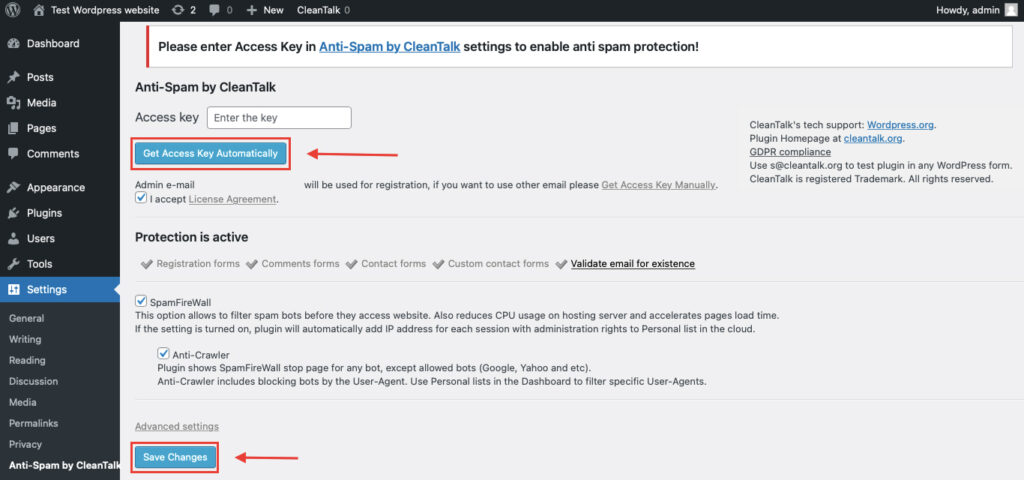
By default, the system keeps the feature disabled. To turn it on:
- Go to in your WP Dashboard → Settings → Security by CleanTalk.
- Click on Genetal settings tab.
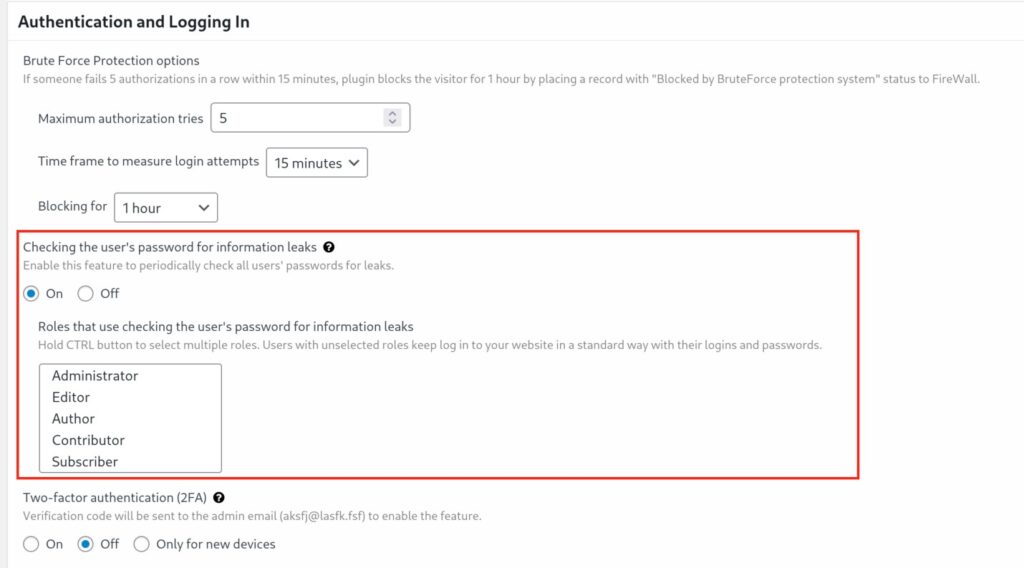
- In the Authentication and Logging In section, select and enable the option “Checking the user’s password for information leaks.”
- Select which roles to cover. By default, the system includes Administrators and Editors.
- Run a one-time scan in Users to get an instant baseline for current accounts.
Why It Matters: WordPress Password Leak Protection
According to OWASP, exposed credentials are among the most dangerous security risks for web applications. Even strong passwords become unsafe once they appear in leak databases. Password Leak Protection reduces this risk by stopping logins with compromised passwords and requiring users to reset them before continuing.
Next steps
Update your CleanTalk Security Plugin to the latest version.
Enable Password Leak Protection in Authentication → General Settings, choose the roles to cover, and run a one-time scan in Users to check current accounts.
If you want to strengthen your defenses further, combine Password Leak Protection with CleanTalk Anti-Spam to stop bot registrations and spam comments, and with Uptime Monitoring (ссылка) to keep track of your site’s availability around the clock.
FAQ
Which roles are checked by default?
By default, Password Leak Protection applies to Administrators and Editors. You can extend coverage to other roles in Authentication → General Settings.
Does Password Leak Protection send email alerts?
No. Notifications appear in the WordPress dashboard as a banner and as statuses in the Users table. There are no email alerts for leaked passwords.
If a password leaks, the system blocks the login. On the next attempt, it redirects the user to a reset form on the login page. After the user confirms a new password, the system marks their account as safe again..
How does this feature work with Brute Force Protection and 2FA?
Password Leak Protection complements brute force defense and Two-Factor Authentication (2FA). Together they stop both guessed and compromised passwords, reducing the most common login risks for WordPress sites.
To explore more ways of keeping your site secure, check out our guide on CleanTalk Security Plugin tools for WordPress